of small businesses plan to increase their use of technology platforms
77% plan to adopt emerging technologies in their infrastructure.

of small businesses have no dedicated cybersecurity measures in place
A common mindset among entrepreneurs is that their businesses are too small to be targeted.

of all organizations suffer at least one ransomware attack per year
Over 50% of small businesses impacted by ransomware end up paying the ransom.

of people say they would stop doing business with a company that has been breached
87% of small business possess customer data that could be compromised in the event of a data breach.

Digital transformation of the economy and the increase in cyber threats go hand in hand
Organizations of all sizes are embracing technologies like cloud computing, artificial intelligence, and the Internet of Things to improve their productivity and efficiency. However, not everybody knows how to implement security controls for their information technology, and many remain in the dark about the risks presented by much of their technology. Not only this, but taking the initiative to implement cybersecurity measures can be daunting and confusing to many business owners.
This framework was built to provide easy to learn, yet comprehensive guidance on cybersecurity measures for small business owners who are concerned about the safety of their assets and reputation.
The Framework
Compliance Checklist
The following document contains a list of all cybersecurity controls that must be implemented to comply with the UMPI CyberLadder framework. The checklist can also be used to perform a gap analysis on the current state of your organization's network vs the required state of the CyberLadder framework. In addition to the PDF below, you can access the checklist as a Google Doc here.
 Loading...
Loading...
Benefits of Using The CyberLadder Framework
For small business owners, it can be frustrating trying to find resources for cybersecurity. Many popular cybersecurity frameworks are geared toward middle to large-sized companies. They also often assume the reader has a technical background. The UMPI CyberLadder Framework is geared towards those who want a simpler, ground-up guide to improving their organization's security.

Frequently Asked Questions (FAQs)
Who Is This Framework For?
The CyberLadder is a framework designed to help businesses of any size implement a quality cybersecurity program to protect themselves, their customers, and their assets. The framework is industry-neutral and can be applied to environments of all sizes and styles. From a single individual running an online store as a side hustle, to an accounting firm comprised of 20+ employees, the security tips and guidelines specified in the CyberLadder are applicable.
Does This Framework Guarantee 100% Security?
No framework from anybody is going to guarantee 100% security because 100% security is not possible. Even if you implement all the best cybersecurity controls, there is going to be a new vulnerability introduced tomorrow that applies to your network. Since the digital landscape is evolving so quickly, there is always going to be an element of risk present to using computers and the Internet. However, you can harden your business systems and network as much as possible by implementing the security controls and plans recommended in this framework and others. But at the end of the day, these controls will not be effective unless they are combined with common-sense practices when using technology.
Where Do The Tips In This Security Framework Come From?
When building this framework, I gathered all the controls and best practices taught to me in my education as well as some of the advanced concepts recommended in professional frameworks like ISO 27001, CIS, and NIST. I started with a huge amalgamation of technologies, strategies, and controls, then outlined them into a hierarchical framework and simplified them in a way that can be understood by business owners without a significant technical background.
Do I Have To Implement Every Control Outlined In This Framework?
No, you don't. This framework can be implemented in any way you like. You can pick and choose which policies and controls you implement based on their application to your specific case. Some controls may not apply to your business, for example, not every small business has an online e-commerce shop. However, I do recommend that you perform a Gap Analysis on your network environment and implement any controls that are missing. This way, you can get as much protection as possible for your business.
Key Concepts
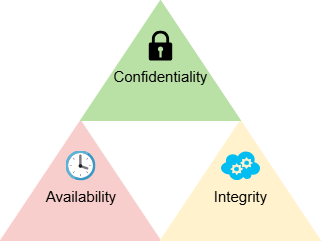
CIA Triad
The CIA Triad is a basic model for cybersecurity that outlines the three key principles to be protected: Confidentiality, Integrity, and Availability. A good cybersecurity program should protect the confidentiality of private data, the integrity of data and network operations, and the availability of the technical resources needed for daily operations.
AAA Framework
Another basic model used in cybersecurity is the (A)authentication, (A)uthorization, and (A)ccounting framework. These three concepts form the basic strategy for implementing secure identities and access within an organization. Every organization should have a reliable method by which employees authenticate themselves to company resources, a stable system for authorizing the employees' levels of access, and an ongoing process for monitoring their sessions and collecting data about their actions within the resources.

Zero Trust
Technology and data are no longer confined to a single network residing behind a secure perimeter. Technology is decentralized, with a wide variety of services, networks, and platforms involved in just a single organization. Because we can no longer rely on just a secure perimeter for protection, a model called Zero Trust has emerged. In a Zero Trust architecture, three guiding principles are applied to every corner of the digital landscape: verify explicitly, use least privilege access, and assume breach. A common tagline for Zero Trust is "never trust, always verify".
Defense In Depth
Defense In Depth is an approach to cybersecurity that acknowledges the sophistication of modern threats and seeks to protect assets with multiple layers of security. A DiD approach will apply security controls at various points to make it as difficult as possible for an attacker to fully compromise an asset.
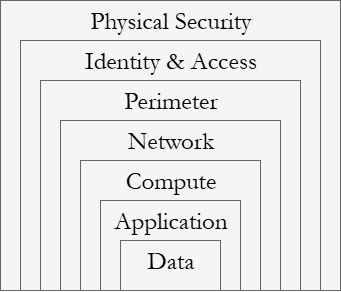
Cyber Kill Chain
To effectively defend against cyber threats, you need to understand how they work. The Cyber Kill Chain is an industry standard model that breaks the typical cyberattack down into seven stages. This breakdown allows cyber defense to be approached from various points in your organization's digital infrastructure. By using the structure of the Cyber Kill Chain, you can alleviate some of the chaos that comes with trying to address an attack head-on.
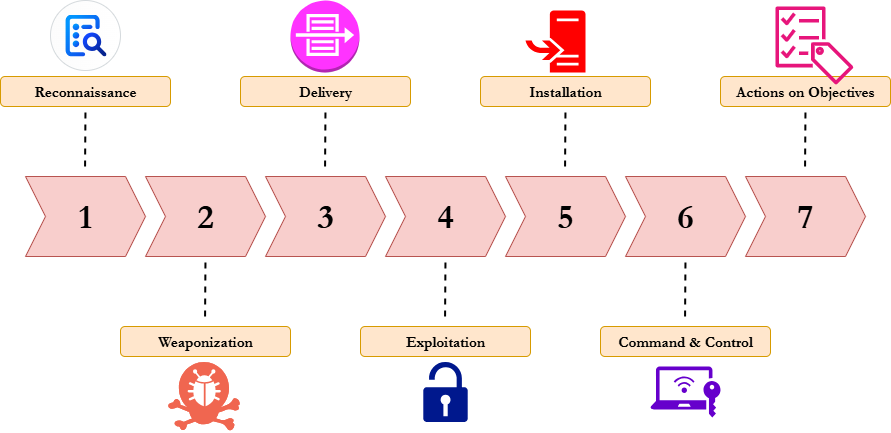
Pyramid of Pain
Even the most skilled of hackers are bound to leave behind evidence at some point. These artifacts, along with certain behaviors observed in compromised networks, make up what we know as Indicators of Compromise (IoCs). By proactively searching for IoCs and scheming ways to counter them, you can bring your organization's cybersecurity posture to another level. The Pyramid of Pain is a model that lists common IoCs from the most visible at the bottom to the most sophisticated at the top. Corresponding with each level is a measure of how difficult each IoC would be for an attacker to change if uncovered.
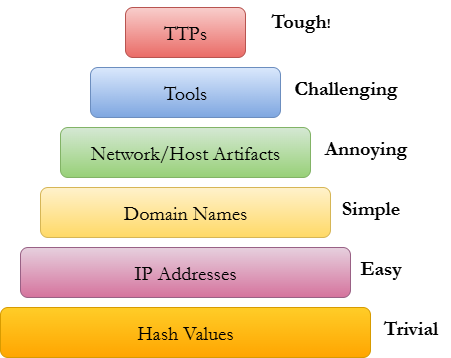
System Development Lifecycle (SDLC)
The increased use of technology in businesses has led to the need for well designed, smooth running systems to accomplish workflows. Just like all the personnel in a project, all the components of a system need to come together for objectives to be met. A poorly designed system, just like a poorly assembled team, can create a world of hurt for the bottom line. The Systems Development Lifecycle (SDLC) is a framework for properly implementing a system, from its genesis to its continuing maintenance. Following this pre-set lifecycle allows business leadership to organize system development into stages, with one flowing directly into the other. This way, systems development projects can be kept in scope and on schedule.
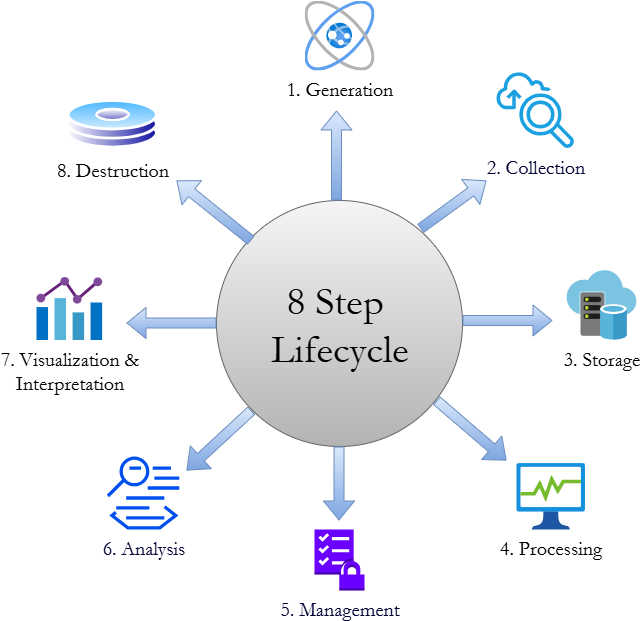
Data Lifecycle
Every organization produces and processes large amounts of data every single day. This data encompasses everything from employee and customer records to purchase orders to digital advertisements. Data is perhaps an organization's most vital asset. How an organization cares for its data can make or break it. Every day, threat actors across the globe devise new schemes to get their hands on important data and use it for their own ends. To get a stable grasp on your organization's data security, you can use the Data Lifecycle, which presents a standard list of tasks for properly managing data in your organization, from creation to disposal.
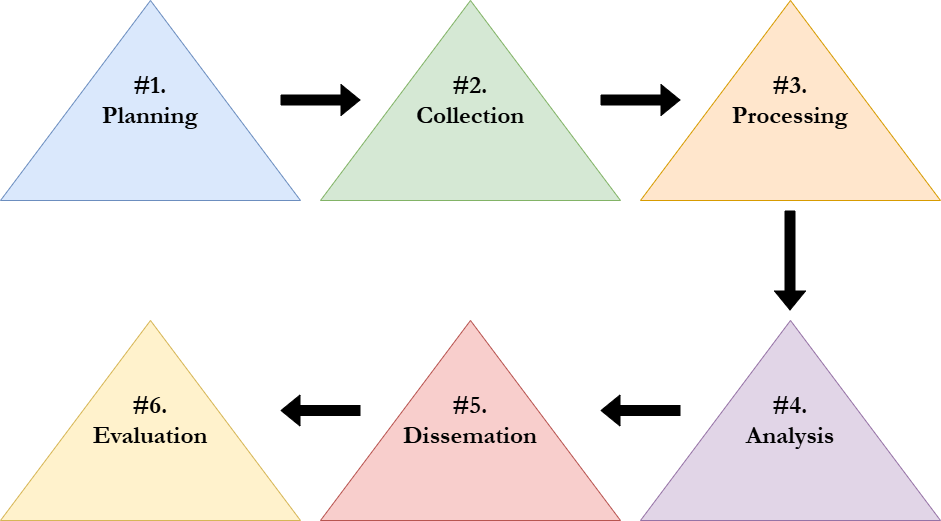
Security Intelligence Cycle
A great way to keep your business up to date with the latest cyber threats is by tracking and studying various threat intelligence sources. Threat Intelligence is data regarding potential or existing cyber threats. It usually includes Indicators of Compromise (IoCs), the Tactics, Techniques & Procedures (TTPs) of threat actors, and detailed analysis of any exploits and payloads. As a small business owner, you can keep up with threat intelligence through a variety of sources; it can be as simple as studying the front pages of major cybersecurity news websites every morning, and as deep as setting up servers to collect intelligence from major security analytics sources. By following the Security Intelligence Cycle, you can design a program for clear collection, analysis, and sharing of threat intelligence in your workplace.
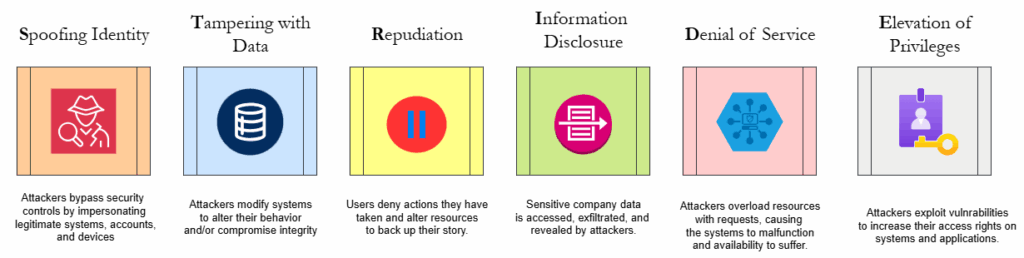
STRIDE Threat Model
A business owner can become overwhelmed trying to find and address all of the cyber threats present in their network. The STRIDE Threat Model is a methodology for categorizing cyber threats. The name is an acronym comprising the six specific threat categories defined by the model. They are: Spoofing identity, Tampering with data, Repudiation, Information disclosure, Denial of Service (DoS), and Elevation of privileges. These six techniques are the most common cyber threats one may find themselves vulnerable to. By organizing them in an easy to remember model, a business owner can more easily weed out specific threats in their environment and define the proper measures to address them.