Before you jump right into implementing a cybersecurity program for your business, you need to understand what exactly a cybersecurity program is and what it should contain. A cybersecurity program is a centralized, constantly evolving strategy for providing security governance for your business assets, whether they be people, devices, data, or capital.
All components of a cybersecurity program are dedicated to upholding the Confidentiality, Integrity, and Availability of your assets. These three objectives make up the CIA Triad, one of the most basic cybersecurity methodologies.
- Confidentiality: ensures that an organization’s data is protected from unauthorized disclosure, whether intentional or unintentional.
- Integrity: ensures that resources are protected from unauthorized tampering and modification.
- Availability: ensures that critical resources are highly available and have a degree of resistance to errors and offer good performance and usability to end users.
A cybersecurity program is made up of both technical and non-technical measures. Technical measures include things like antivirus software, firewalls, encryption, and backup/restore. Non-technical measures include policies, procedures, and audits.
Every organization is different. Especially in small businesses, the number of employees and their associated roles and responsibilities will greatly vary. Some business owners opt to outsource their technological needs to third parties, while others hire an in-house person or handle their tech needs in-house. Regardless of the business size, every cybersecurity program must uphold the CIA Triad, and more often than not, they will all be implemented in the following stages:
- Define the scope of the cybersecurity program and what assets/resources it will cover.
- Document and rank the assets according to the risk they pose to your business if they are ever compromised.
- Implement controls for securing the assets.
- Monitor, audit, and improve the entire security program over time.
A good cybersecurity program needs to start from the top. Good security practices need to be implemented within the business management and then worked down the chain into the lowest-level operations. This is done by starting with high-level security goals and then breaking them down into granular controls and policies.
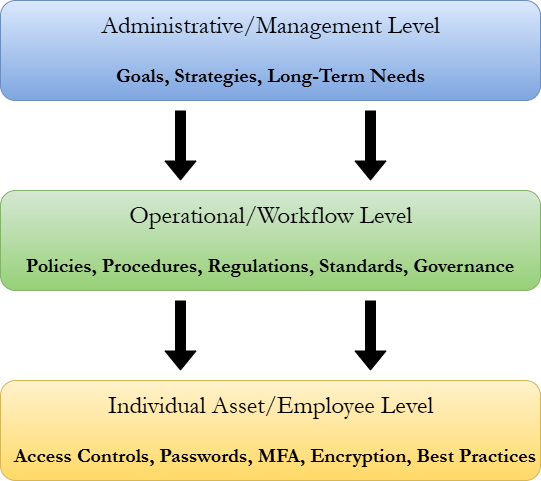
Controls are the cybersecurity technologies and policies that enforce the goals defined in the cybersecurity program. Cybersecurity controls can be broken down into three categories:
- Administrative: cybersecurity policies, procedures, standards, playbooks, guidelines, training, project management, and workplace conduct regulations.
- Technical: access controls, encryption, identity and access management, security hardware, and enforcement mechanisms.
- Physical: locks, perimeter security controls, intrusion monitoring, and environmental protections.
This framework provides information on various controls from all three categories. An effective cybersecurity program needs to consider each category equally. Some may have the preconception that cybersecurity only involves technical matters. If you only opt for technical controls and ignore administrative and physical controls, gaps will appear in your cybersecurity coverage almost instantly, and over time, these gaps can become so large that they render the technical controls completely ineffective.
Developing a cybersecurity program is an iterative process and will take time. This framework does its best to cover all the most critical areas and needs of small business cybersecurity. However, you will rarely address every major concern in the initial implementation of the program. You need to approach your cybersecurity program with continuous improvement in mind and ensure that you have the resources and time available to regularly audit and sharpen controls and skills as your business needs evolve.
