Just all aspects of business, individual digital assets work together to perform desired services to the organization and its stakeholders. Having a router is useless, unless you have a WAN connection to provide Internet, which is unless you have a subscription to an ISP to provide said connectivity. Hardware, software, networks, identities, and data all depend on each other to function and perform as expected. Since you are preparing to implement a cybersecurity program to protect your organization’s assets, it helps to get a holistic view of how each piece of digital infrastructure fits into the bigger picture. Dependency Mapping is a task that accomplishes this and will help you prioritize assets for security controls in future stages.
A dependency map is a logical chart that breaks down your cybersecurity components from the high-level systems and goals to the small individual components and software. The map shows how components of all sizes work together and flow up to accomplish major cybersecurity goals.
Let’s use the following example of a small business cybersecurity program:
My small business is an accounting firm with five employees and five workstations. The computers run Windows systems managed by Intune. Identities are managed using MS Entra ID. We have a basic SOHO network with a file server that hosts internal data. We also have a backup server that stores weekly backups of systems and data. We use BitLocker on all workstations and encryption at rest for the shared drives to protect our customers’ financial information.
We can break this down into a dependency diagram like this:
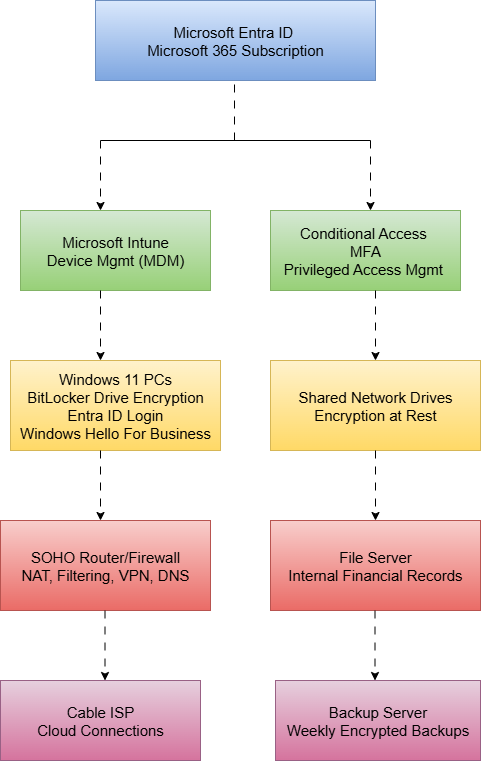
If you know the key processes and systems in your business environment, then the dependency maps should flow pretty smoothly. Don't worry about being perfect the first time around. It will take a few iterations to get all dependencies down and clearly mapped. Having this map will make implementing future parts of this framework easier. Knowing how every piece of technology chains together will help you with business impact analysis, risk assessments, and prioritization of security controls.
