Phishing
Phishing attacks have consistently been one of the most popular cyberattacks directed at small businesses. Just about everybody with an email account has received a phishing email before. These attacks use social engineering tactics like inventing a fake scenario, impersonating an authority figure, or threatening retaliation against the victim users. These are done to coerce the victims into performing an action that results in damage to the victim and their associates, and gain for the attacker. In most cases, the ultimate end goal of the threat actor is financial gain.
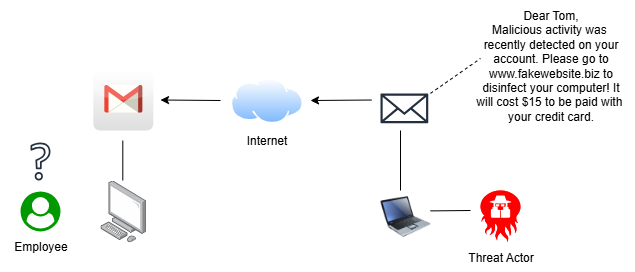
Many phishing emails are easy to identify. Key indicators include significant misspellings, source email addresses lacking a company domain, and requests to perform actions that no organization would realistically ask you to do. However in recent years, phishing emails have gotten more sophisticated. Much of this has to do with the emergence of Generative AI, which can write realistic error-free messages with better chances of convincing users. Phishing is going to continue to be a major cyber threat moving forward, with small businesses remaining an ideal target.
Subcategories of phishing:
- Spear-phishing: more targeted phishing attacks aimed at specific high-value individuals in an organization.
- Whaling: similar to spear-phishing, but specifically targets high-level executives.
- Vishing: uses voice calls to coerce victims into revealing sensitive information.
- SMSishing: uses text messaging as its message delivery platform.
- Pharming: redirects victims to a malicious website mimicking a real one.
Ransomware
Ransomware caught the public's attention in the 2010s, with several high-profile strains like Cryptolocker and WannaCry wreaking havoc across the globe. Since then, ransomware strains have become a dime a dozen, with small businesses being a major target. Ransomware infects an organization's network through methods like malicious email and drive-by downloads. Once inside the network, the ransomware encrypts the victim's files, rendering them unreadable. The threat actor will demand a ransom to be paid by the victim to decrypt their files. If the ransom is not paid within a set time frame, the threat actors often promise to destroy the decryption key, rendering the files permanently unreadable. Sophisticated ransomware can spread from one system to others on the network, infecting all hard drives, network drives, and removable media it finds.

Ransomware has sprouted into its own black market. Ransomware as a Service (RaaS) is a model that allows less experienced threat actors to subscribe to a ransomware provider that will provide them with ransomware software. The threat actors can then use this software to attack their targets of choice. This model allows anybody to launch sophisticated ransomware attacks without writing a single line of code. A determined competitor to your business could use a ransomware subscription to damage your assets while denying direct responsibility for it. The possibilities presented by RaaS are very concerning to both private enterprises and world governments.
Data Breaches
Providing goods and services to your community inherently produces large amounts of data. Data has become one of the most valuable assets possessed by businesses. The way data is used, processed, and stored can make or break a business. Most businesses possess some form of Personally Identifiable Information (PII) of customers and employees. This data is sacred to an individual, and misuse of it can have significant consequences. Unfortunately, data breaches continue to rise in frequency, with enterprises of all sizes serving as enticing targets. Data breaches occur as a result of a successful cyberattack that allows attackers to compromise an organization's systems and exfiltrate data. In some cases, an organization may not even be aware that its business data has been published.
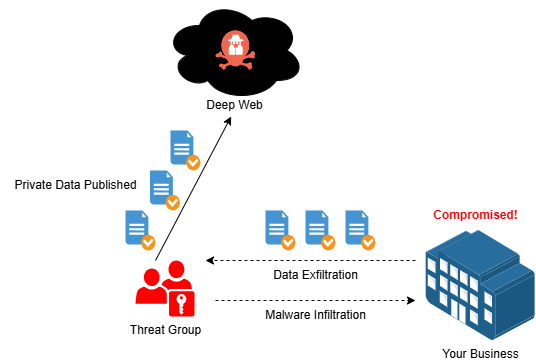
A data breach can have catastrophic consequences for your business. Customers who have their private data exposed through an attack on your business will likely lose trust in you and cut off their support. If it is found that you were negligent in your handling of data, legal consequences can be brought upon you. These consequences can be extremely difficult to recover from.
Password Attacks
Passwords are a universal requirement in today's digital world. As a business owner, you likely have a dozen or so passwords for different websites, applications, and services used in your daily workflow. Passwords are well known as a prime target for compromise by an attacker. Compromising just one account password can create endless opportunities for attackers to pivot and escalate their privileges within your digital assets.

Some common password attacks include:
- Brute Force: This attack involves using high amounts of computing power to try every possible combination of characters against an account until the correct password is found.
- Password Spraying: Involves firing off a collection of commonly used passwords against multiple accounts to identify and compromise the one with the weakest password.
- Dictionary Attack: Similar to password spraying, this attack tries a series of passwords containing dictionary words against a target to uncover the correct one.
- Rainbow Table Attack: This attack uses a collection of pre-determined cryptographic hash values to identify a password's hash value and unlock the account with it.
- Credential Stuffing: This attack involves an attacker collecting leaked usernames and passwords from a data breach and targeting a specific user's current accounts with those same credentials, hoping they never changed them.
Password attacks are a classic technique out of the hacker's playbook, yet they still remain effective due to continued human error and bad practices when creating passwords.
Advanced Persistent Threats (APTs)
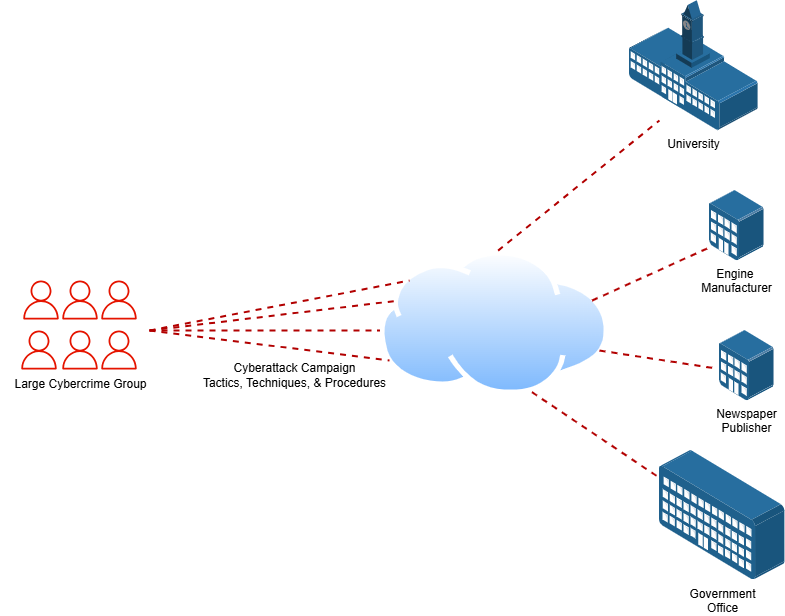
As we look towards the future, there are many emerging cyberthreats that cause great concern. Advanced Persistent Threats or APTs are one such threat that have the potential to do unbelievable amounts of damage. An APT isn't a specific threat, but a series of Tactics, Techniques, and Procedures (TTPs) used by threat groups against targets to cause harm over time. APTs often remain undetected in an organization's network for months and even years. They set up persistence mechanisms within the target network that allow them to leave and return when desired. While inside the target network, an APT can perform tasks like exfiltrating data, corrupting systems, and sabotaging operations. APTs aim to accomplish all of this covertly, even if it means doing a little over a long period. Think of Andy Dufrene in The Shawshank Redemption slowly digging a tunnel out of prison over a span of 20 years. That's similar to how APTs operate.
APTs are usually attributed to nation-state actors or large organized cybercrime groups. Government agencies and large corporations are usually the prime targets for APTs, but small to medium-sized businesses are not ruled out. APTs can selectively target certain businesses based on their industry and relationship with their country's regular operations. This may be done as part of a larger scheme to sabotage a country from the ground up. Journalists and publishers are frequently targeted by APTs looking to disrupt or maliciously influence the flow of information.
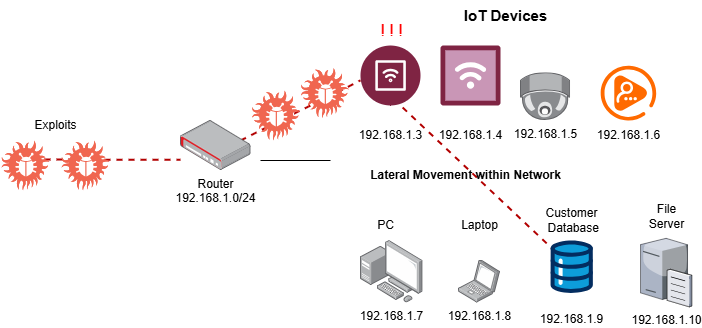
IoT Attacks
One of the most exciting new technologies gaining traction today is the "Internet of Things". IoT is made up of a range of small devices that use micro-controllers and sensors to control everyday appliances and tasks. HVAC systems, security cameras, kitchen appliances, locks, lights, and vehicle components can all be digitized and connected to networks where they can be controlled and configured remotely. While IoT devices can greatly enhance business operations in many areas, they present serious risks in others. IoT devices are well known for containing a disproportionately high amount of security vulnerabilities. This stems from their relatively new presence, the limited computational power they possess, and the presence of open ports and default passwords in many devices. IoT devices produce large amounts of data that can be collected and stolen to be used for nefarious purposes.
Since many small businesses only configure one network segment to host all of their devices, they end up placing insecure IoT devices in the same segment as their critical data and machines. This is possibly one of the riskiest configurations in modern networking, and will certainly have dire consequences for your business if exploited.
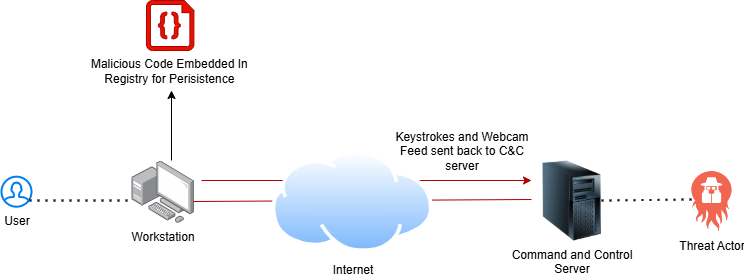
Remote Access Trojans (RATs)
A Remote Access Trojan or RAT is a particularly frightening and insidious cyber threat. RATs are typically downloaded unbeknownst to the affected user. They disguise themselves as legitimate files and then infect target systems when the file is executed. The RAT will then immediately create a backdoor in the system to enable a connection back to the threat actor's Command and Control (C2) server. Once this is established, threat actors will be able to perform a variety of nefarious activities on your system, such as infiltrating sensitive data, logging keystrokes to steal credentials, and laterally moving to other systems on the network. RATs can also enable threat actors to turn on your computer's webcam and exfiltrate your browser history for potential blackmail or as a show of power. The stealthy nature of RATs and their capabilities have established them as one of the most insidious cyber threats in the 2020s.
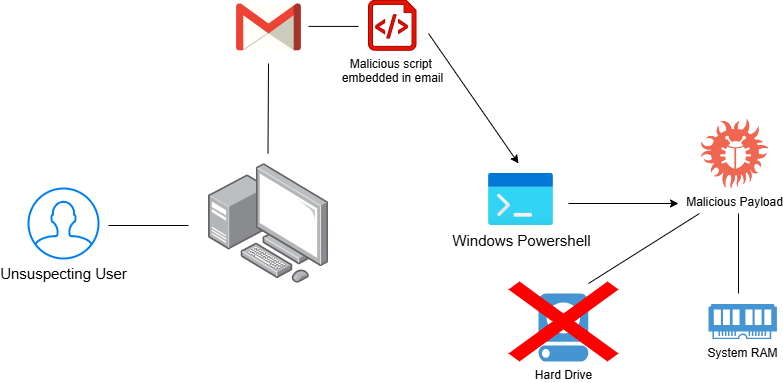
Fileless Malware (Living Off the Land Attack)
Most of us are used to traditional malware that spreads through files residing on target systems. When the file is executed, the malware's payload is delivered to the victim's machine. Malware grows more sophisticated by the year, and a special new breed has emerged in recent years. Fileless Malware does not attach itself to any machine files; instead, it resides completely in the target system's RAM. Since these programs don't write to the machine's storage, antimalware programs may not detect them. Fileless malware uses the same entry tactics as any other piece of malware, such as phishing emails or drive-by downloads. The malware will then take advantage of built-in system services such as PowerShell to gain a foothold in system memory and begin executing its payloads. Further system services, such as WinRM, allow the malware to begin searching for other network targets for lateral movement and privilege escalation. Due to its stealthy nature and appeal to hackers, fileless malware is a major cyber threat to keep an eye on moving forward.
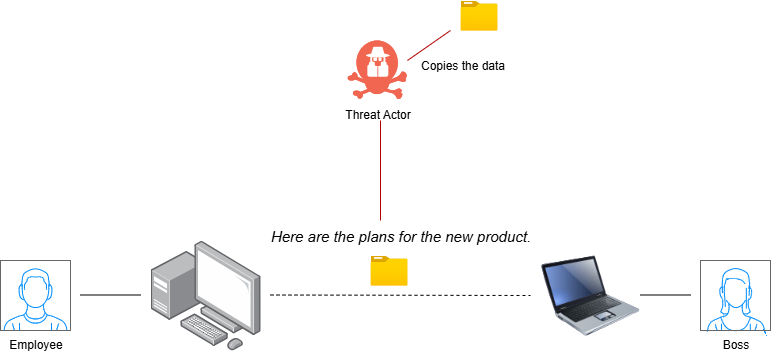
Man In The Middle (MITM) Attacks
We like to believe that the data we send back and forth to our associates is safe and private, for our eyes only. However there is always the possibility that the data we exchange is being seen by a third actor in the session, one we do not want there. This is the basic concept of a Man in The Middle (MiTM) Attack. If a threat actor happens upon an insecure network, they may set up a form of snooping that captures data being exchanged between unsuspecting users. The users are unaware that their data is being viewed by a malicious third party who at the same time is copying and exfiltrating the data from the session. There are many specific types of MiTM Attacks. Rogue Access Points occur when a threat actor installs their own wireless network that imitates the valid company Wi-Fi. Unsuspecting employees then connect to the malicious Wi-Fi, allowing the threat actor to view all traffic. ARP, DNS, and IP Spoofing all occur when a threat actor manipulates network traffic to make it appear as if they are the legitimate owners of a specific MAC, IP, or domain. Users then send their traffic to the threat actor, thinking they are going to the intended owner of the address. Cloud IAM platforms and web applications can have their user sessions hijacked so that threat actors can view all traffic being exchanged between users and the online resources. MITM Attacks are a covert, sneaky threat that can have devastating consequences for a business. They highlight the need for data encryption in transit, secure session management, and the implementation of Zero Trust environments.
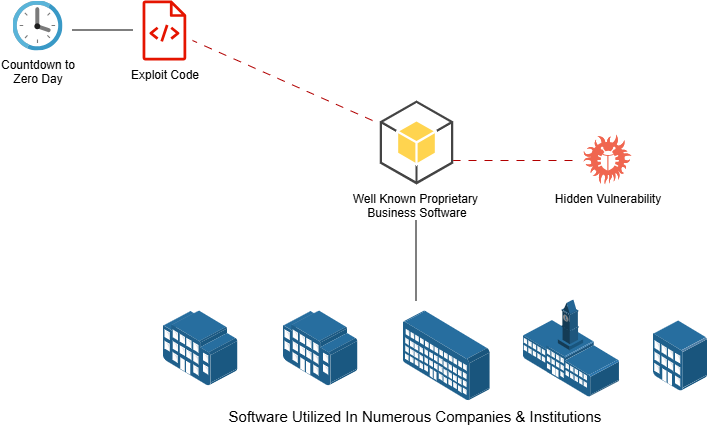
Zero Day Exploits
Most businesses utilize several reputable pieces of software to perform their workflows on. Whether these programs are proprietary or open source, on-premises or cloud based, they all have the potential to lead to serious security incidents and cause great harm to their customers. The people who program popular software are human just like everyone else, and they have the potential to make mistakes. Sometimes they are not aware of these mistakes until it is too late. Zero Day Vulnerabilities are security weaknesses in programs that are known only to a specific threat actor. After discovering the vulnerability, the threat actor can prepare an exploit to attack all instances of the software spanning numerous organizations. At the same time, the software developers are unaware of any of this, thus having "Zero days" to fix the security vulnerability. Once an exploit is developed, threat actors can unleash their campaign of terror and do serious damage to users of the unfortunate piece of software. Since by design, zero day exploits are unknown until they are taken advantage of, business owners can feel helpless and paranoid of every new program and patch they install on their systems.