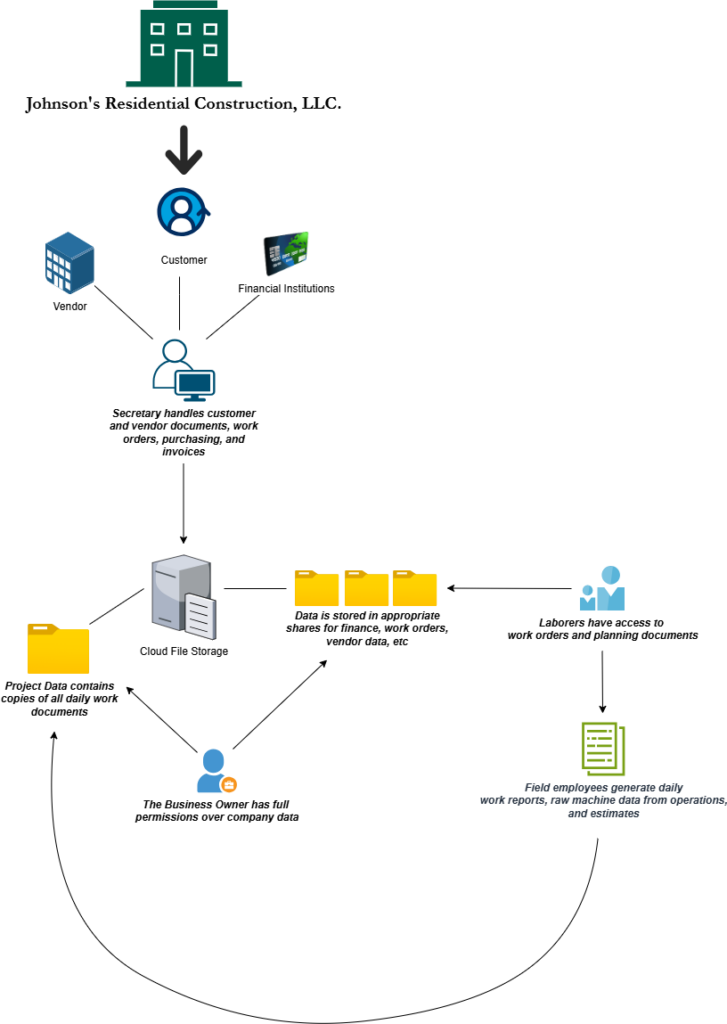
In a digital landscape that is increasingly decentralized, one of the best ways to narrow down your cybersecurity needs is to document the regular data flows that take place throughout your business environment. Every business has regular workflows that its employees perform with company technology. For example, your secretary may interact with vendors and customers, sending and receiving documents and handling financial transactions. These pieces of data may then be stored in a secure storage location, with access given to the business owner and accounting staff. We have a series of data flows here: the flow of data from external parties to the secretary, the movement of data from the secretary to the company storage devices, and the retrieval of the data from the storage by higher-level management.
Depending on the size of your business and the relevance of technology to your daily operations, you may have only a few regular data flows or many. Documenting these data flows will help you narrow down where security is lacking, where the most sensitive data/operations exist, and what areas need to be prioritized in the cybersecurity program. Documenting data flows is an extension of the inventories you should have already made in this stage of the framework. Hardware and software asset inventories, data classifications, network maps, stakeholder identification, third-party inventories, identity/access management, data flow documentation, and dependency mapping all combine to provide a top-down view of your business technology landscape. Having this holistic view will make planning and implementing security controls much smoother.
You do not have to use a super professional approach to document data flows. Like the physical network map, you can use a basic drawing program like draw.io or Microsoft Paint. You can even draw out your data flows physically. Ensure that you keep the records in a safe and secure location, alongside the other network/system inventories created during this stage and update them as workflows and systems change.
Below I have provided an example basic data flow illustration for a small construction company.