It is very rare for any business to maintain the exact same people in the exact same roles for a long period of time. There are always going to be transfers, resignations, firings, and new hires. With employee identities being reflected heavily on digital resources, it is just as important for businesses to conduct periodic reviews of employee digital rights in the same way they would conduct in-person job reviews. If a business does not have a dedicated IT staff, it can be very easy to assign employees privileges and forget about them. This will result in privilege leak further down the road, with employees migrating roles and responsibilities and taking privileges with them that they should no longer have.
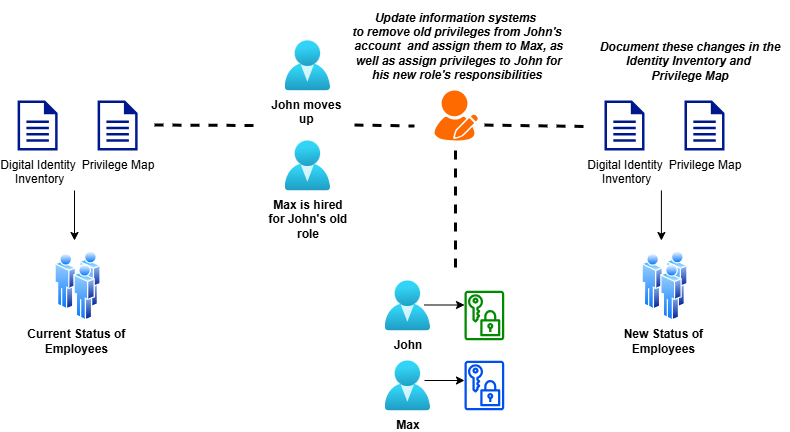
In Stage 1 of this framework, you were directed to make a comprehensive inventory of all digital identities present in your environment, as well as separate documentation of the privileges and rights assigned to these identities. In Stage 2, you were directed to create professional guidelines for onboarding and offboarding employee accounts. This documentation is a circle back to those documents, which should be done annually, as well as anytime there is a change in employee status.
Make sure to carefully study the identities and permissions that you have documented and compare them with the current job descriptions of the employees. If you have changed jobs to include new tasks while removing others, the digital identities for those employees should be changed to reflect the necessary privileges. For example, say you hire a dedicated Human Resources employee and remove the HR tasks from your company secretary. In that case, you will need to remove all HR related privileges from the secretary and migrate them to a new identity for the HR employee.
Anytime changes are made to digital roles and responsibilities, you will need to update the identity inventory and privileges map to reflect them. In essence, this is an instance of the repeatable nature of a cybersecurity program, as you are required to circle from Stage 4 of the framework back to Stage 1. Always make sure that you retain previous versions of the identity and privilege inventories, properly noted so that they can be restored if necessary. In cases where a change of employee status involves the departure of an employee and/or the hiring of a new one, you will need to invoke the Onboarding/Offboarding guidelines to make sure the process is secure. Invoking the onboarding/offboarding processes will also require you to modify the identity and privilege documentation to reflect the removal of one identity and/or the addition of another.