If you implement new cybersecurity controls in your business environment, you may take for granted that everything is going to work well. Controls, benchmarks, patches, appliances, and programs are all provided to end users to perform as intended right after configuring. However, there are always bound to be hiccups in the implementation of new technology. Many times, these hiccups are specific nuances within your environment that can be mitigated with the help of online documentation. However, it can be very inconvenient for the progress of your work if you have already implemented a security control and realize that an adjustment needs to be made afterwards. Scope creep is bound to erupt, and you may find yourself having to roll back installations and start from scratch.
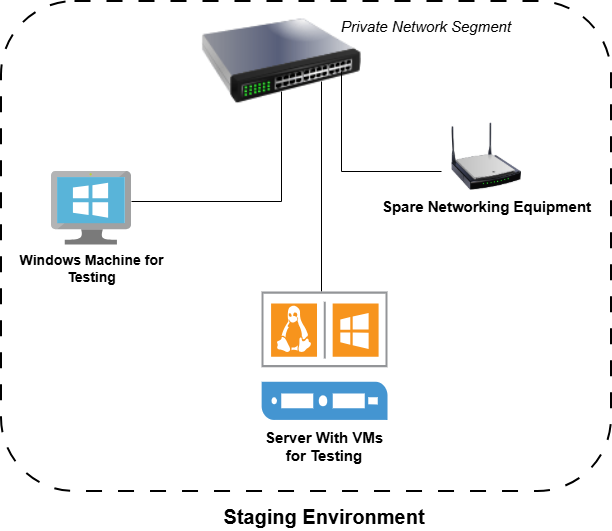
This risk can be mitigated or, at the very least, controlled by using a staging environment. A staging environment is a small air-gapped environment featuring mockups of your actual digital resources on which you can test new applications, updates, and controls before rolling them out to your actual infrastructure. This way, you can observe how the different pieces of your cybersecurity program will function and document any issues that will need remediation. A staging environment does not need to be too complex. You could roll out a few virtual machines containing copies of your workplace operating systems and applications, and test major host-level changes on them before implementing. An even simpler approach would be to keep a dedicated spare laptop on hand and run through tests on it before network-wide installation. For network-level testing, you could set up an extra switch, or even a dedicated network segment, and test configurations there before greenlighting installation on the core network. For example, if you are planning to implement 802.1X authentication on your network with RADIUS, you could try the setup in the test environment first to troubleshoot any connectivity/authentication hurdles early on.
Creating a staging environment may seem like a bunch of extra work, but it can save you from lots of pain further on down the road. It is up to you to pick and choose which security implementations need testing. However, this framework officially recommends testing any security technology that you are uncertain about implementing and don’t have 100% confidence in configuring correctly. For example, you may have perfect confidence in your ability to set up a SOHO router and select the proper security settings. However, you may be less confident in your ability to configure VLANs on a managed switch. In this case, it is fine to proceed with setting up the router, but it is advisable to run through the VLAN setup a few times in your staging area to ensure you get it right. Some business owners may be completely unfamiliar with information technology and feel the need to test out everything before implementing it. This is completely fine; it is much better to slow down and take the time to become familiar with different cybersecurity controls rather than rushing into the Implementation phase and running into chaos due to a lack of preparation.