At its core, cybersecurity is all about identifying and managing risk. The biggest mistake made by many small business owners is believing that they are too small to face any serious risks. Every business of every size will be faced with a handful of different risks throughout its lifespan. Some businesses face more risks while others face less; this depends on many factors, such as the company size, industry, and value. Risks come from all directions, but in the case of this framework, we are concerned with the sub-category of cyber risk. In this section of the framework, you will learn how to conduct a cybersecurity risk assessment and get an idea of how these risks can be managed.
A risk assessment is one of the most powerful and important documents in a cybersecurity program. Much of the work you will do in later stages of this framework will be decided by the results of your risk assessment. Before beginning the assessment, you need to be familiar with several terms:
- Risk: the potential for a threat to exploit a vulnerability resulting in an impact on your organization.
- Threat: an event that could jeopardize your organization and its assets
- Vulnerability: a weakness in your organization’s assets, either known or unknown to you.
- Exploit: the means that a threat uses to take advantage of a vulnerability
- Payload: something that is executed after an exploit has taken advantage of a vulnerability
- Asset Value: the relative value of an asset to your organization, measured in either monetary or qualitative value
- Probability: the likelihood that a threat will exploit a vulnerability.
- Impact: the effect on your organization if a risk materializes.
- Control: a process undertaken by your organization to reduce risk.
The basic formula used to calculate risk is: Risk = Probability * Impact
After reviewing these definitions, you likely already have some ideas about what risks exist to your organization. A risk assessment will serve as a comprehensive review of all organizational risks, including those that may not be immediately apparent. Once you have identified the cybersecurity risk posed to your organization, you can start ranking and prioritizing them for remediation.
There are two main types of risk assessment: quantitative risk assessment and qualitative risk assessment. A quantitative risk assessment uses math and thorough reviews of your assets to put risks down in numbers. A qualitative risk assessment relies on expert opinion and analysis to identify risks, resulting in risk classification levels of high, medium, and low. You can specifically choose one type of risk assessment to perform, but generally, a small business risk assessment will be a combination of both quantitative and qualitative.
To perform a successful risk assessment, you will need to follow the steps listed below. The structure used to conduct a risk assessment is known as the Risk Assessment Policy (RAP). Luckily for you, a lot of the material needed for the risk assessment has already been determined in previous framework sections, such as the asset inventories.
Determine Scope: Risk assessments will be conducted at various times and locations. A risk assessment can be conducted on everything from the entire organization to a single process or system. This documentation assumes that you will conduct a comprehensive, first-time risk assessment of your organization’s entire technology landscape. However, you can and should conduct more continuous and in-depth risk assessments on different aspects of your organization moving forward. A standard rule of thumb for a great cybersecurity program is to conduct a risk assessment after a cyber incident occurs and after a new system or process has been implemented. Besides defining the physical and logical scope of your assessment, you should prepare all employees and stakeholders by clearly communicating with them and establishing channels for keeping them informed throughout the assessment.
Identify Assets: If you have followed along with the framework up to this point, you already have a thorough inventory of your organization’s digital assets. These include hardware, software, data, processes, and network topology. This documentation assumes you are performing a full initial risk assessment. In that case, you will need to combine all of those asset inventories and list them out so that you can clearly identify what needs to be assessed. However, in the future, you will likely need to zero in and perform dedicated risk assessments on specific areas, such as individual systems or data flows. In that case, you will need to list out the assets specific to those areas.
Determine Each Asset Value (AV): In all honesty, you are likely to be disinterested in addressing cybersecurity risks unless there is a dollar sign attached to each one. This is why quantitative risk assessments are important, as they will spell out for you what awaits your budget in the event of a cyber-attack. Therefore, you will want to calculate the Asset Value (AV) of each asset listed in the previous step. This step may require you to do some additional discovery to obtain financial documents relating to the purchase/maintenance cost of each asset. The total asset value will be a combination of the Purchase Cost of the asset, the potential Replacement Cost of the asset, and the Depreciated Cost, or the original purchase cost of the asset reduced by aging factors. You may need to do some close observations of the assets, as well as interviews with employees familiar with the day-to-day operations of the assets, to get the best total asset value.
Categorize Assets by Criticality: Once you have your digital assets listed and assigned an asset value, you have the necessary means to categorize and rank them according to criticality. There should be three levels of criticality to choose from: critical, major, or minor. It is important to have the asset values quantified and listed before doing this, as it helps you get a full, unbiased view of the true criticality of each asset. You may be surprised that assets you assumed were irrelevant actually have a huge impact on your business operations, while assets you thought were important are actually easier to replace than you thought.
Identify Threats & Vulnerabilities: After identifying, quantifying, and categorizing your assets, you can begin identifying threats and vulnerabilities. It is unlikely that you will identify all of them on the first try, which is why threat and vulnerability identification is a continuous process. Do your best to take into consideration all of the major threats and vulnerabilities that may impact your organization. To be as accurate as possible, research recent cybersecurity news, especially that involving your industry, to find the most prevalent emerging cyber threats. You can assemble the most recent vulnerability scan of your network infrastructure to further narrow down the most prevalent threats to your organization, specifically. If you feel unqualified and uncomfortable performing any vulnerability scans, you can look into having a qualified employee do it or hiring a contractor that specializes in cybersecurity. Beyond just old-fashioned hacking and malware infections, you also have to account for internal threats such as system failures and human threats, both accidental and malicious. Also assess your area's proximity to major natural disasters that could physically harm or destroy your assets. Don’t worry about how messy your list looks. What is important is that you study your assets closely and list all the associated vulnerabilities and threats you can find.
Quantify Risks: Once you have quantified asset values as well as thorough assessments of the vulnerabilities and threats facing said assets, you can perform some calculations to quantify the probability of a risk materializing, as well as the impact this would have on your business.
- The Exposure Factor (EF) of an asset is the expected amount of loss if a risk materializes. This is calculated using careful analysis of the existing security controls in place, along with the ones that are lacking. If you can expect that a breach of your network file server will result in 60% of your internal data being compromised, then the EF would be listed as 0.6.
- The Annualized Rate of Occurrence (ARO) is calculated by the likelihood that a threat will take advantage of a vulnerability in a given year. Historical records of your business or other businesses of your same size and sector will help calculate this. If you can expect, after thorough research, that your business can expect three data breaches per year in its existing state, then the ARO is 3.
- The Single Loss Expectancy (SLE) is the product of the asset value and the exposure factor. It gives you an estimate of how much financial loss can be expected from one attack on your asset. Let's assume that the total calculated value of your internal file server is $14,000. We calculated the EF earlier and came up with 0.6. So we calculate $14,000 * 0.6 and come up with an SLE of $8,400.
- Finally, the Annualized Loss Expectancy (ALE) is the final calculation of expected financial loss from a risk over a given year. It is the result of the product of the SLE and ARO. We just found out that a data breach on an internal file server has an SLE of $8,400. We also know that the ARO for this specific risk is 3. So we calculate $8,400 * 3 and get an ALE of $25,200.
Assign Severity Levels to Risks: Now that you have quantified risks to your business and gained a good idea of the damage they could cause, you can break them down into severity levels to influence remediation. There are a number of ways this can be done. In almost all risk assessments, risks can be qualified as Low, Medium, or High based on a combination of their probability and impact. In the last step, you produced figures that lay out the cost to your organization that each risk will produce. You will want to set a "yardstick" that determines what cost qualifies a risk for what category. For example, you may decide that a low-level risk is anything with a possible cost that is under $500, a medium-level risk is anything between $500 and $1,000, and a high-level risk is anything over $1,000 in cost. Since we are talking about a small business, here it's pretty likely that your yardsticks will be even lower than this. Regardless of what standards you set for risk categorization, you will want to assign each uncovered risk to a category. Once all risks have been categorized, you have the remediation priority pretty much spelled out for you. High-level risks come first for remediation, followed by medium and then low.
A common tool used in this process is the risk matrix, which is a visual chart that denotes likelihood on one axis and impact on the other. Risks are placed on the chart according to their likelihood rank and impact rank, and use the resulting intersection for prioritization.
The Likelihood axis typically looks like this:
1: Highly Unlikely
2: Unlikely
3: Possible
4: Likely
5: Highly Likely
The Impact axis will then look like this:
1: Negligible
2: Minor
3: Moderate
4: Significant
5: Severe
This will produce a risk matrix looking something like this:
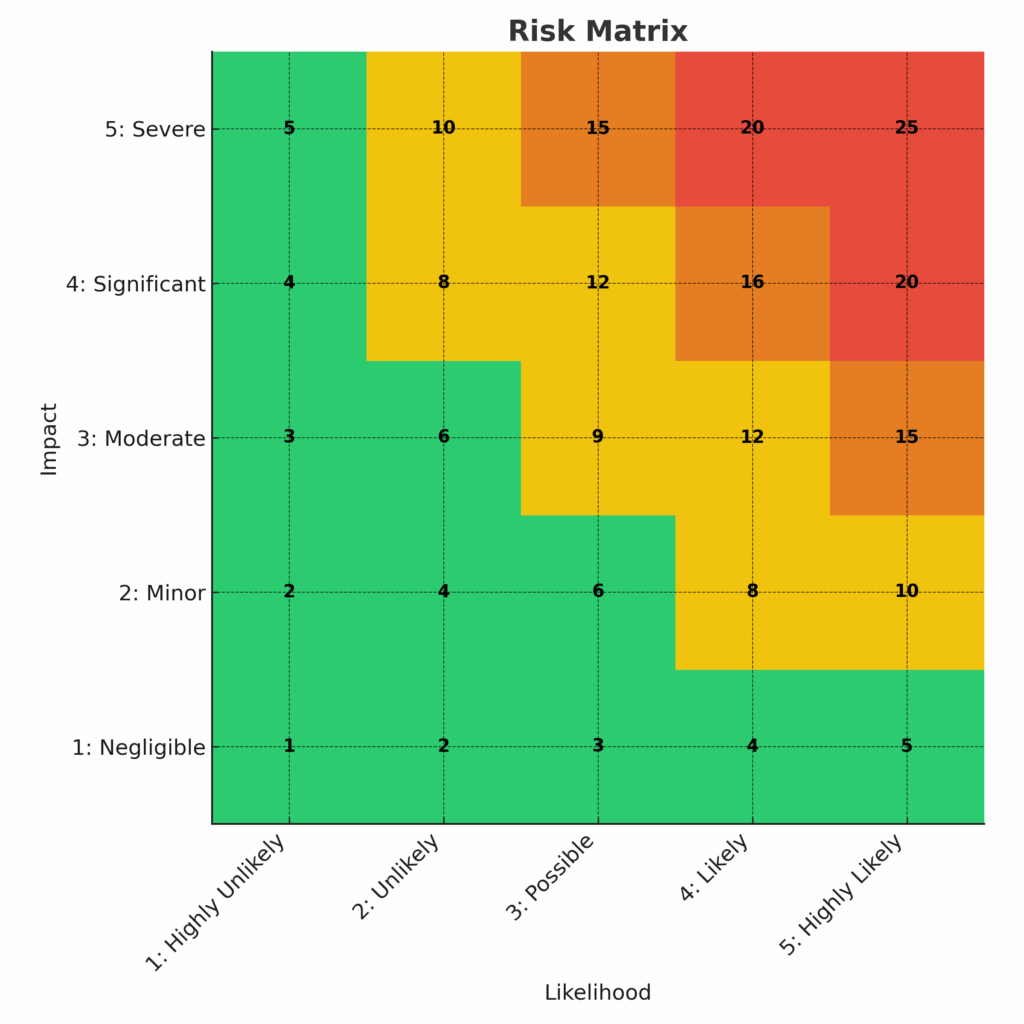
The risk matrix is more in line with a qualitative risk assessment, as it uses basic estimates of probability and impact to rank risk severity. However, it is just as usable for this qualitative risk assessment. You should use the calculations you made for ARO, SLE, and ALE to determine the Probability and Impact levels.
In addition to the risk matrix, it is advised to create a risk register, which is a spreadsheet that serves as an organized list of all identified risks, as well as information about the risk's priority, decided mitigations, and the employees who are assigned to manage the risk. The risk register is a vital document for the next stage of this framework, where you will plan which security controls to implement, when they will be implemented, and how they will be implemented. For optimal risk organization in your organization, share your risk register with your Steering Committee and all appropriate employees to keep everyone aware of risks and enable collaboration for planning remediation. Feel free to use the risk register template provided below.
 Loading...
Loading...
Determine Appropriate Security Controls: It may take several iterations of the previous steps before you have comfortably prioritized your cybersecurity risks. This is perfectly acceptable, and it is important to remember that your goal is to uncover and assess as many cybersecurity risks to your organization as possible, regardless of how long and/or messy a process it is. Once you have a solid register of risks, you can begin implementing security controls to address them. These security controls can be any of the ones highlighted in the future stages of this framework, as well as any outside of this framework’s documentation. The important thing is that they effectively address the risks. If this is your first time implementing any cybersecurity controls into your organization, it is acceptable at this point to shift gears to Stage 3 of this framework in order to determine what controls you will need to address what risks. Just make sure that when you finish identifying appropriate controls, you return to this documentation to finalize your risk assessment.
The methods and controls (or lack of) that you choose to address risks can be categorized under one of the following Risk Management Strategies:
- Risk Avoidance: Rather than trying to implement controls to protect against a risk, you simply change your business practices to avoid the risks altogether. For example, if you have a public-facing web server residing on your network and discover that it faces a large number of risks, you may decide to get rid of your self-hosted website altogether. This strategy is used when the cost of implementing controls to address the risk is too high and inconvenient.
- Risk Acceptance: If a risk is low probability and low impact, you may decide that it is easier to accept the chances of it occurring rather than spend potentially large amounts of money addressing it. Use this approach with caution for obvious reasons. For example, you may have Remote Desktop Protocol (RDP) enabled on all of your internal workstations for remote assistance across your business. RDP is not enabled through the public Internet. If an attacker compromises your network, they have a pretty easy path to use RDP for lateral movement. Your alternative is to buy a professional TeamViewer license instead. You decide that the chances of an attacker making it all the way into your internal environment are low enough, and that you don't have the money to pay for a TeamViewer subscription. Therefore, you accept the risk and continue using RDP in your internal environment.
- Risk Mitigation: Even if the risk cannot be fully eliminated, you can implement controls to reduce the likelihood of it being exploited. Most of the cybersecurity controls you will implement in Stage 3 fall under this umbrella. You usually can never 100% eliminate the risks, but you can significantly reduce the attack surface. For example, you can close all ports on a public web server except the necessary ones, and install a Web Application Firewall (WAF) to reduce the chances of attackers exploiting the server.
- Risk Transference: Sometimes, you may decide it is difficult for your organization to try and address every risk, and that it is in your best interest to give the responsibility to somebody else. This may entail purchasing Cyber Insurance or hiring a Managed Security Service Provider (MSSP).
Monitor & Document Results: once you have implemented necessary security controls, you must monitor them to determine their effectiveness. No matter how thorough you think your risk assessment and subsequent control implementation is, there is always the possibility that it will be ineffective and exploits will still slip through. This is why risk assessment is a continuous process, there will always be controls that can be tailored and replaced for better security. And even if you have successfully addressed all of the risks in your first assessment, there are bound to be new ones that emerged as a result of the changes made to your environment in the previous step.
By now you should have a rough understanding of the stages that make up a risk assessment. Once again, it is essential to understand that this is not a one and done thing like many other pieces of this framework are. Risk assessments need to be conducted frequently to ensure your organization’s cybersecurity stays continually hardened.
Example Risk Assessment
 Loading...
Loading...
