Defining clear roles and responsibilities regarding IT and cybersecurity in your business environment is a critical precursor to implementing an effective cybersecurity program. If responsibilities are not clearly distributed, then the cybersecurity program will disintegrate as soon as it is tested. You need to know who is responsible for resources, who is responsible for upholding defensive measures, and who is responsible for incident response and recovery. Since this framework is tailored directly to small business environments, there is room for flexibility in the designation of roles and responsibilities. Since a small business can comprise anywhere from two to a few hundred employees, all of these roles/responsibilities may be shared between two employees, or they could be independently designated to a dozen or so. Regardless of how you divide up the roles and responsibilities, make sure that you clearly document them and make sure the employees are aware of and regularly review them. Also, make sure to include specific responsibilities in job descriptions so that future employees are aware of the IT/cybersecurity-specific responsibilities they will have to perform at your organization.
Security Administrator
This individual is responsible for ensuring that the business environment is up to date with security requirements and upholds the Confidentiality, Integrity, and Availability of customers and employees in all areas of business. During the implementation of the cybersecurity program, this individual will do much of the installation and fine-tuning of technologies and controls. In addition to the proper implementation of the program, the Security Administrator is responsible for helping employees with security concerns, and reviewing the program and its associated controls to ensure security measures are ongoing.
IT Systems Administrator
While the Security Administrator is focused on upholding the Confidentiality, Integrity, and Availability of company resources, an IT Systems Administrator is responsible for keeping company assets like hardware, software, and networks functional. An IT Sysadmin needs to have good communication and customer service skills, as they will be responsible for troubleshooting technical issues in real time. When hiring an IT Sysadmin for your business, make sure to create a very detailed job description that highlights the specific technical requirements of your digital environment. If you use all macOS devices, make sure to put that in print. If your environment is almost entirely cloud-based, you will want to highlight cloud computing as a main skill.
Information Technology Manager
While the previous two roles were technician-level roles, the IT Manager is responsible for overseeing the business side of IT and cybersecurity activities. In the context of implementing a cybersecurity program, the IT Manager leads the charge on much of the rest of Stage 2. Drafting and tailoring plans and procedures, managing IT budgets, and communicating with vendors are some of the key responsibilities of the IT Manager. The security admin and sysadmin roles report to the manager, who acts as a liaison between them and the business owner. In many small business scenarios, the IT Manager role is taken on by the business owner themself.
Incident Response & Business Continuity Manager
Every business needs to be prepared for a cyberattack to happen. It is becoming practically guaranteed that some sort of major cyber crisis will affect any given business at some point in its lifetime. This is why strong Incident Response, Disaster Recovery, and Business Continuity Plans and Procedures are paramount in a cybersecurity program. An Incident Response/Business Continuity Manager works vigorously to implement and tailor business activities to meet the latest cyber threats. They need to be good with crisis management and communication, and have a good knowledge of security tools and specific business workflows. They also work in close collaboration with the Security & IT administrators to plan and implement new tools and technologies.
Data Owner
A Data Owner is exactly what it sounds like, someone who takes the full ownership of the data in a business or a specific department. A Data Owner is generally not an entire role in of itself, rather a responsibility grouped with other managerial responsibilities. If you are the owner of a small business with only a few employees, then you, as the owner, will likely be the Data Owner for all data transmitted, processed, and stored in your network. However, if your business is larger with a number of different departments, then you will want to assign the manager of each department as the designated Data Owner for that department's datasets. The data owner is responsible for their data from the beginning to the end of its lifecycle. They assign security labels to the data and dictate plans for how it is to be handled. If a specific dataset is comprised, then its data owner is held responsible.
Data Steward
Data is the new oil; it is the most important asset possessed by every business. Thus, data needs good protection. We have already established a Data Owner, who is an individual responsible for the management of specific datasets and categories. However, in larger businesses with vast amounts of complex data flows, a data owner cannot take all the burden of maintaining the data on themselves. This is where a Data Steward comes in. The data steward keeps the quality of data up to organizational standards. This is done under the direction of the Data Owner and other leadership roles. The data steward handles the business side of data security, planning workflows and lifecycle, implementing and monitoring data policies, and implementing standardization and quality assurance. Like the data owner, the data steward isn't usually a specific role, but a responsibility that is part of a larger role. Therefore, data stewardship can be combined with other IT/cybersecurity roles, such as the IT Manager.
Data Custodian
While the Data Steward is responsible for the business side of data assurance, the Data Custodian is responsible for implementing the technical data security controls. The custodian takes the policies passed down to them by the owner and steward, and implements the necessary controls to meet the standards set forth by those policies. They manage the storage devices used to store the datasets and handle backup and restore operations performed on them. They also apply access controls, encryption, and monitoring capabilities to enforce the confidentiality and integrity of data. Again, this is a specific responsibility rather than an entire role, and in a small business environment, it is likely to be taken on by the Security Administrator or IT SysAdmin.
As stated earlier, these roles may need to be combined for some individuals, depending on the size of the business. The security administrator and data custodian have similar roles with overlapping knowledge, as do the IT Manager and IR Manager. If you feel that the responsibilities listed are out of scope for your organization, you can look into outsourcing them to a third-party IT department and/or Managed Security Service Provider (MSSP).
Once you have designed and assigned cybersecurity roles for your organization, it is important that you develop a system for how each of the roles will communicate. Attacking security issues and events requires a system of triage, where different individuals uncover said issues and rank them based on the necessity of their remediation before escalating them up the chain to the next individual.
For example, your security administrator may uncover a malware infection running rampant throughout your network. As soon as they have confirmed it, they notify the necessary parties and escalate control to the IR Manager, who eradicates the infection and performs a forensic analysis on its causes. This information is passed to upper-level management, who then have the data custodian and security administrator work together to design and implement new controls and policies to address the vulnerabilities that enabled the infection. The data steward ensures that the new policies are properly enforced, while the IT Sysadmin adapts the network infrastructure to the new controls.
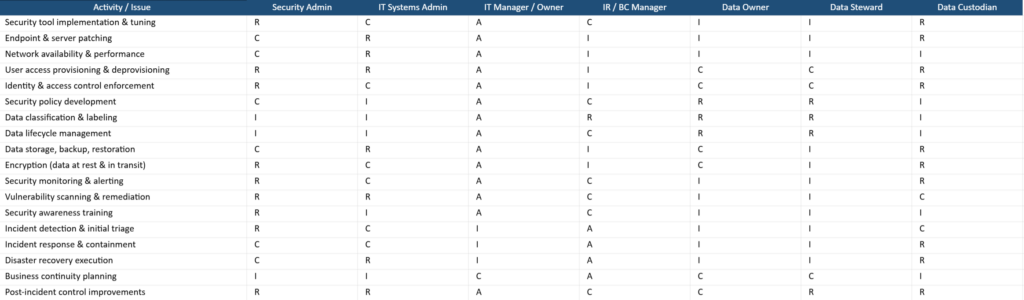
You can utilize the template provided below to keep documentation of the assigned cybersecurity roles in your organization. Ensure that this documentation is securely stored with other internal company files and is regularly updated to reflect turnover and role changes. It is also a good idea to create a Responsibility Assignment (RACI) Matrix to visually reflect these roles and responsibilities. A RACI Matrix categorizes roles and responsibilities by assigning them one of the following four categories: Responsible, Accountable,Consulted, and Informed. Creating a RACI Matrix will be especially helpful if your environment has a staff that takes on many different cybersecurity roles per person. Below is an example RACI Matrix that reflects the basic roles and responsibilities outlined in this documentation.