This framework highlights several best practices for keeping user authentication and authorization as secure as possible. Multifactor Authentication and Passwordless Authentication are two major technologies that can help enhance security for your workplace identities. However, your business may manage resources that are so sensitive that further precautions are desired. There is always the risk of insider threats to be considered. For example, you may maintain an on-site database of customer financial and health information. If you give a single employee access to that data for their job, you are essentially creating a single point of failure. Even if you trust that one employee to the moon and back, there is always the chance that someday they could go rogue and use their privileges for nefarious reasons. Numerous security controls exist to help mitigate this risk, such as Data Loss Prevention and Continuous Monitoring of User Sessions.
Another effective control is Dual Authorization. Instead of assigning a single employee access to sensitive resources, you could split the task between two different employees. In dual authorization, you require that both employees be present for access to be granted. Instead of giving access to a single employee’s user account, you would create a dedicated service account specifically for the sensitive resource, something like “Data Retrieval Acct #1”. You would then mandate multi-factor authentication for that account and split the authentication factors between the two employees. The other employee would have no knowledge or access to the factor that the other possesses. When a task needs to be done on the sensitive resource, the first employee would provide the first authentication factor for the service account, and then the second employee would provide the second authentication factor.
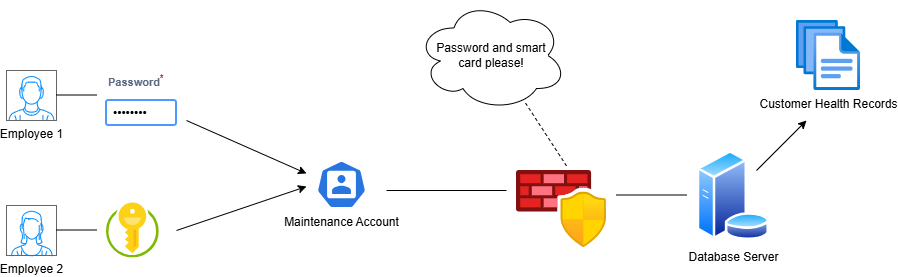
For example, let’s say that Beal’s Hygiene Services is a dental clinic that has a database of medical records for its customers. The database server sits on an isolated network segment behind a firewall with a service account called “Maintenance” enabled for data management tasks. The administration at Beal’s is concerned about insider threats and has concluded that the customer PHI is too valuable to risk in the hands of a single employee. Therefore, they give the password for the account to Mary, who is the customer records manager, and a smart card to John, who is the in-house IT technician. When maintenance needs to be done on the customer database, both Mary and John need to be present for access to the Maintenance account to be granted. While there is always the chance that Mary or John individually would hatch a scheme to steal the customer data, the chances of both of them scheming together are much lower.