It’s often said that cyberattacks are not a matter of “if” but a matter of “when”. Any organization that regularly engages with network technology will inevitably experience a cyberattack at some point. New tactics and pieces of malware are developed by threat actors every day, and even the best cyber defenses on the market may not always be able to keep up.
It is essential to have plans in place to address cyber incidents when the day comes quickly. This area of cybersecurity is known as Incident Response (IR). Several standard Incident Response life-cycles provide a basic guide for implementing IR. All life-cycles usually look something like this:
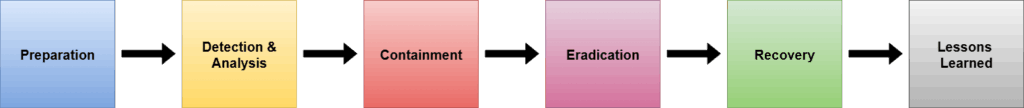
Preparation: A baseline security configuration is in place, as well as a chain of escalation that can be easily followed by all employees when an incident is suspected.
Detection & Analysis: When a suspicious event arises, the Indicators of Compromise (IoC) are detected quickly, either by user observation or automated tools. The information is forwarded to a party responsible for analyzing these IoCs to confirm their validity. This can also be done with a combination of careful human observation and automated tools such as Artificial Intelligence, virus scanners, and Threat Intelligence websites.
Containment: If the Analysis phase confirms the existence of a cyber threat, the Containment phase needs to engage quickly. Most small businesses do not have a dedicated Security Operations Center, so this phase will need to be a collaboration between the reporting employee, the manager/admin who confirmed the attack, and any on-site technical professional. This phase may also require contact with a third-party IT professional if one is utilized. Containment measures usually involve activities like disconnecting affected hosts from the network, disabling infected user accounts, and blocking attacker IP addresses from further contact.
Eradication: Once an active attack has been contained, eradication activities can be implemented. This usually includes using anti-malware tools like Malwarebytes, cleaning up temporary files and registry entries, and even completely re-imaging hosts.
Recovery: Once eradication has been confirmed, recovery methods need to be implemented. If an attack is caught and eradicated early, this could be as simple as reconnecting a host to the network or re-enabling a user account. However, if the attack damages any assets, the recovery phase will be much more complicated. This could include restoring files from backups, updating web filtering blacklists, and implementing extra network controls.
The Recovery Phase may also go beyond technical recovery. If severe attacks occur and infiltrate sensitive data, public relations measures will need to be invoked. This could include notifying stakeholders, releasing a public statement to customers, and even bringing in law enforcement.
Lessons Learned: When an incident has been fully resolved, the workplace cybersecurity team should gather to discuss the incident in detail. Artifacts from the incident, such as malware scan results, threat intelligence reports, and eyewitness accounts, should be archived and brought to the meeting. The cybersecurity team should perform an autopsy on what went wrong, what went right, and what needs to be implemented to mitigate future incidents of a similar type.
Simply following some form of the Incident Response Lifecycle will ease some of the chaos associated with a cyberattack. To further this sense of preparation, the cybersecurity team should develop Incident Response Playbooks.
Playbooks are a step-by-step guide to the actions to take in the event of a specific cybersecurity incident. Every cyberattack requires different steps and methods, so organizing a dedicated playbook for each event is essential.
In earlier tasks listed in this framework, you ended up with knowledge of what kinds of malicious attacks your organization has experienced in the past. Transcripts from anti-malware software scans are handy artifacts in this regard.
Below are some basic example IR playbooks for common incidents I have witnessed in business environments.
Example Plan
Example Phishing Playbook
 Loading...
Loading...
Example Potentially Unwanted Program (PUP) Playbook
 Loading...
Loading...
Copies of Incident Response playbooks should be saved and distributed to the necessary parties involved in the IR process. Playbooks should be updated and fine-tuned to meet new requirements determined from actual incident response activities.
