One of the critical aspects of a cybersecurity program is governance. Without consistent governance, a cybersecurity program will inevitably break down because of non-compliance and non-enforcement in the workplace. In this stage of the Cyberladder Framework, you will find guidelines on how to draft several critical cybersecurity policies for your business environment. However, before you begin drafting individual policies concerning specific controls and strategies, you should start with a Master Cybersecurity Policy.
The master policy will serve as a centerpiece informing your employees and stakeholders how cybersecurity will be conducted in the workplace, and how you plan to align security measures with business objectives. The key is not to go deep into specifics on different technologies and safeguards; rather, you want to set expectations for how people, processes, and technologies will implement cybersecurity in their daily tasks.
The master policy should start by setting a central mission for the organization’s cybersecurity program. At its core, every business-grade cybersecurity program has the same basic goal: to uphold the CIA Triad for the organization. However, for the program to be successful, this needs to be done without compromising the performance and usability of daily business processes. Thus, the mission statement of the policy should be something like to uphold the confidentiality, integrity, and availability of the organization’s data, systems, and processes while aligning all security controls with the core business objectives and key performance metrics.
Cybersecurity needs to touch every department in the organization, regardless of how small it is. From the owners and C-level executives to the third-shift custodians, cybersecurity controls are going to be required at some point in their daily operations. It is important to drive this point home in the policy text to ensure that all employees understand they are required to comply.
Next, the policy should begin outlining the key controls, policies, and technologies implemented in the organization for cybersecurity purposes. Remember that this is a “master” policy, and later you will develop individual, granular policies for specific controls and technologies. Therefore, you don’t have to go into detail in this document; just write a few paragraphs on the major cybersecurity processes and controls, and how they will uphold your organization’s security posture while aligning with key business objectives.
The Cyberladder Framework breaks small business cybersecurity down into three distinct stages: Identify & Document, Plan, Implement, and Educate & Test. These three stages can be used to outline the structure of your master policy. For example, the illustration below breaks down each Cyberladder stage and the key controls and policies from each one.

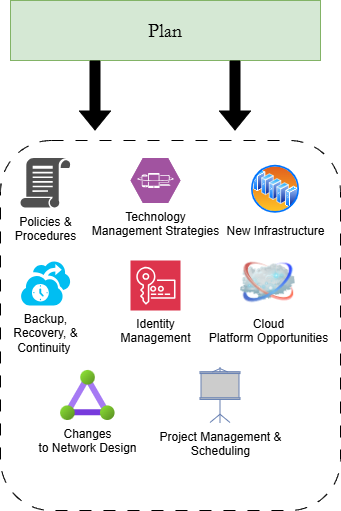
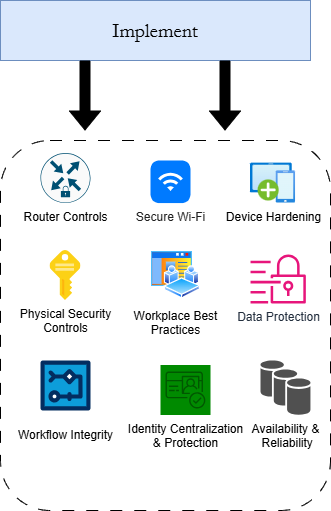
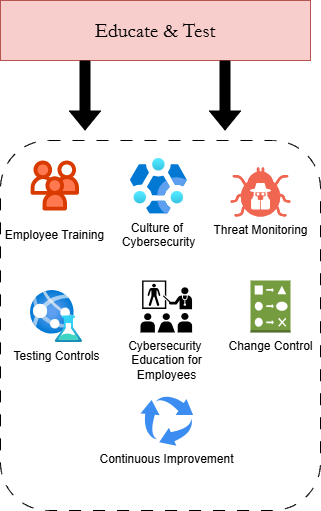
Your employees and stakeholders should get a comfortable idea of what the cybersecurity program will consist of and how it will function, without boring them with hardcore technical jargon and explanations. Remember to make sure to emphasize how the cybersecurity controls and policies will help achieve key business objectives.
The next section of your policy should be an overview of the roles and responsibilities within your business that are responsible for upholding the cybersecurity program. We have already dedicated a previous section of the framework to this. You can simply summarize the key points from that section. Make sure to include employees who will perform each role, their professional contact information, and a brief description of what the role does regarding cybersecurity. Again, every business is going to have a different arrangement for these roles. One business may have one person performing all the roles, another may split responsibilities between several employees, and another may have all of it completely outsourced to a contractor. Just make sure the policy clearly states who will uphold the key cybersecurity responsibilities.
At this point, your master policy is coming together and is a solid outline of what your business cybersecurity program will contain. However, for governance to be successful, you need to establish consequences for non-compliance. Without being too aggressive, you should ensure that your policy warns of consequences for employee non-compliance with established cybersecurity precautions. This drives home the importance of the policy and convinces employees to pay attention to the specifics of the program.
You now have a solid Master Cybersecurity Policy. This document is the frame within which the rest of the program will be developed. As your organization goes through multiple iterations and revisions of the cybersecurity program, you will need to update this policy and inform your employees and key stakeholders of the changes and their impact on the key business objectives.
