While Mobile Device Management (MDM) is a great way to manage company devices in a more decentralized environment, you may wish to allow even more flexibility with employee devices. Depending on what kind of device management strategy you implement, you may want to allow employees to connect devices that are 100% personally owned to your network. You would want to have a technology like Network Access Control (NAC) implemented as a tradeoff to allowing personal devices. Another technology that should be heavily considered in a scenario like this is Mobile Application Management (MAM).
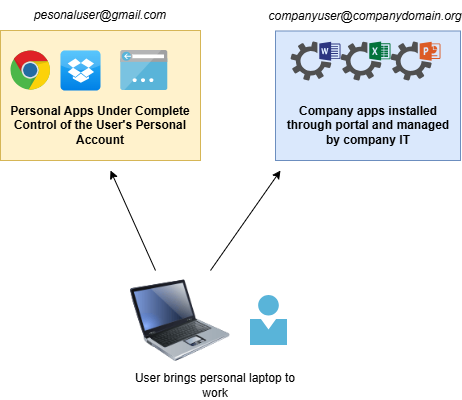
While an MDM strategy places central control of devices in the organization’s hands, an MAM strategy moves a layer up and places control of company applications in the organization's hands, while keeping control over the device with the employee. MAM allows employees to install and use company-specific apps while keeping their devices unenrolled from anything that seizes control of their entire device. However, the apps that are installed under the company’s jurisdiction remain monitored and controlled by the company's IT department.
Probably the most straightforward Mobile Application Management solution is Microsoft Intune App Management. Microsoft allows company leadership to set up a “Company Portal” that allows employees to search for and install from a catalog of pre-selected apps. Once the apps are installed, employees will be directed to connect their work email address to individual applications. Attaching their company identities to the applications places them under the control of the company's Intune solution, while the rest of the device remains under the control of the employee’s personal account.
A common scenario where MAM would be useful is when a company wants to allow users to install Office 365 apps on any device they may need to do their work on the go. The company does not want the overhead of managing entire devices or seizing control away from employees, so they simply upload the Office 365 apps to the Company Portal for the employees to install and use on the go. MAM should be combined with other security measures like Data Loss Prevention (DLP) to further narrow the attack surface for company resources.