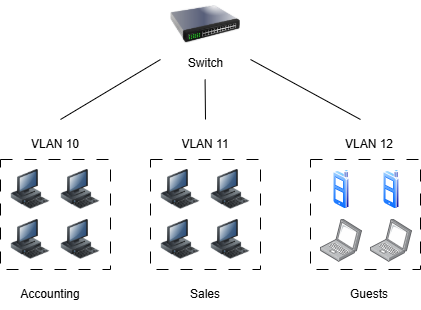
Segmenting networks is one of the best ways to harden your business technology and reduce the damage a cyberattack can cause to your network. Virtual Local Area Networks, or VLANs, are perhaps the most common method used to segment networks. With VLANs, you must keep in mind that a managed switch is required to perform the necessary configurations to create VLANs. Basic plug-and-play unmanaged switches that many small business networks use will not suffice.
When you deploy a switch in your environment, all connected hosts exist in the same Broadcast Domain together, meaning they can talk to one another. VLANs allow you to create multiple independent Broadcast Domains on your network. One broadcast equals one VLAN, and every host assigned to one VLAN can only communicate with other hosts assigned to the same VLAN. So instead of functioning like one big network where every device in every department can see and talk to one another, your environment will now have multiple tiny, segregated networks where devices can only see and talk to devices that fulfill the same criteria as them. For example, you could create a VLAN for Administration, one for Front Desk Staff, one for Guest users, and one for the Development Team.
Not only do VLANs shrink the attack surface of a single network compromise, but they can also help with organizing and monitoring assets by dividing them up and labeling them according to shared criteria.
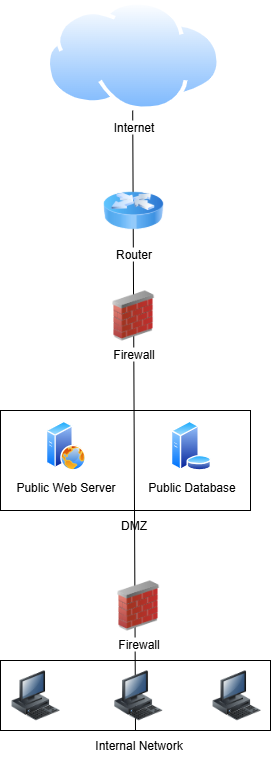
Another method of segmentation is essential for any business that looks to host publicly accessible servers on their network. A Demilitarized Zone (DMZ) is a network segment that sits between the public Internet and your internal network. This segment has public IP connections and its own nuanced security rules. It allows ports to be opened to the Internet so public users can see and interact with your public services running on machines in the DMZ.
Publicly accessible devices have a much higher risk of being compromised. The fact that the DMZ is its own segment means that any compromise will not impact business-sensitive devices residing on the private network behind a router/firewall.
Creating a DMZ usually requires specific configurations on your router, switch, firewall, and potentially all three. Some SOHO routers contain a basic DMZ functionality where you simply provide the IP address of the network device you wish to expose. More advanced network devices usually require a more complicated process.
ALWAYS consult the documentation of your network devices before attempting to configure a DMZ.
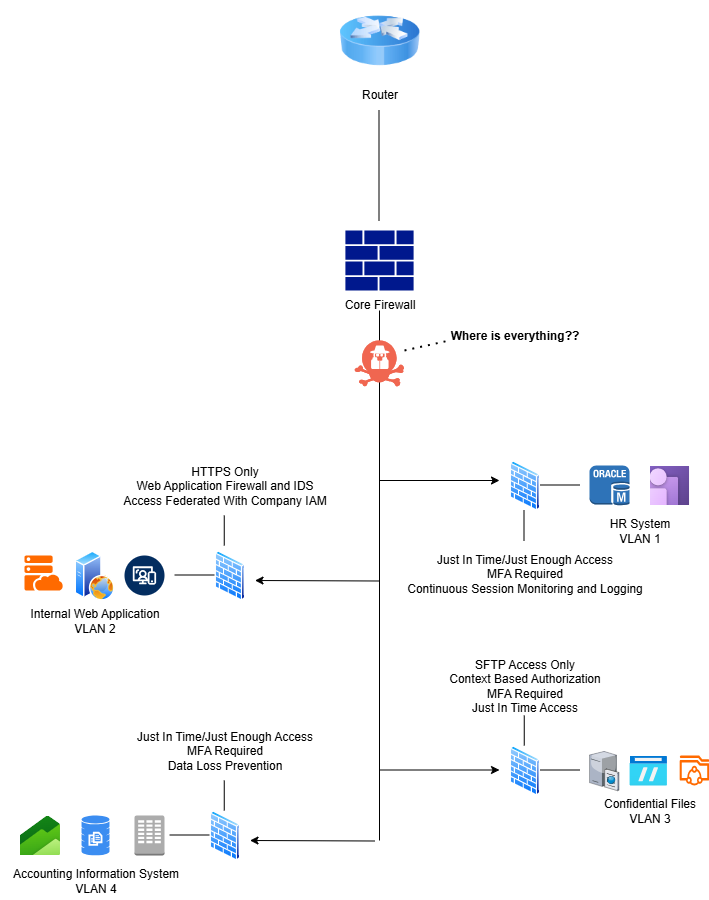
In today's digital landscape, there is a increasing trend of implementing microsegmenation. This strategy takes the idea of segmenting resources even further by creating smaller protected network segments for individual applications, processes, and services. In a typical secure network deployment, you would likely see a single VLAN for all servers, another for employee workstations, and another for ICS/SCADA devices. In a network with microsegmentation, you would see a VLAN for a web app, a VLAN for an HR system, a VLAN for a database server, and a VLAN for a financial data analysis system. Microsegmentation is a key strategy of Zero Trust. We accept that we cannot even trust neighboring servers in our own network, thus we need to isolate individual devices and services to segments for them and only them. Then we can place different security controls in front of each segment, with the controls varying depending on the context of the resources within it. We would want to configure intensive identity and access management controls and encryption on a network segment for confidential files. We would want to restrict open ports to HTTPS for a segment hosting an internal web app.
Microsegmentation can be difficult and pricey to implement, making it appear out of scope for small business environments. However if your organization hosts a wide array of data and services of varying sensitivity levels, it is worth looking into it to drastically increase the security posture of said resources.