Implementing a fresh cybersecurity program for your organization requires a lot of labor and inevitably requires lots of trial and error. Even the most basic of cybersecurity controls can end up requiring long hours of configuration and testing. Like any other business project, there is also the potential for scope and schedule creep.
Before you begin implementing the physical and logical cybersecurity controls specified in this framework, you need to plan heavily to ensure that the project goes as smoothly as possible. You should have already determined the specifics of how you want to implement the applicable technologies from this framework. You may do one big project to implement all changes in one go, or you may decide to take it slow and implement different technologies in phases. Regardless of how you decide to approach project management, you will need to perform Requirements Gathering to ensure you have all the elements necessary for successful implementation.
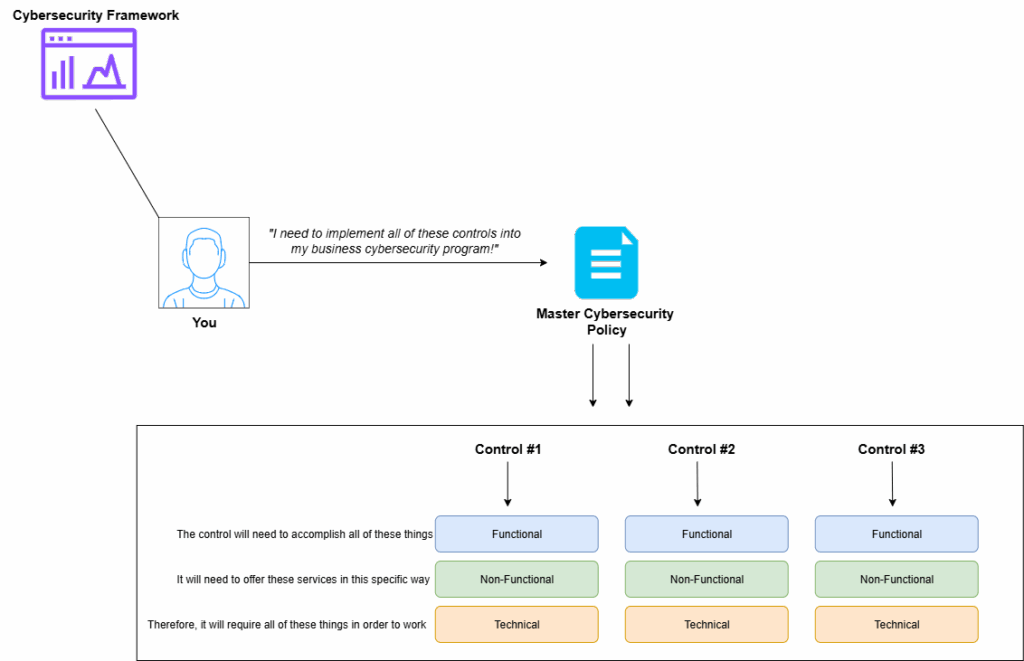
Requirements Gathering is one of the core sections of project preparation. It is where you will define what the project needs, who the project needs, why they are all needed, and what constraints might exist. Requirements for a cybersecurity project will usually require specific pieces of technology, software, licenses, staff, and external contractors.
Requirements Gathering for implementing this framework should consist of the following steps:
Identify Stakeholders: these are all entities that may be affected by implementation of the framework. As the business owner, you have a major stake in the success of the cybersecurity program. If it fails to protect your company data, you could see financial, legal, and reputational ruin. However, if implementation of the framework goes over schedule and results in lots of downtime, you will also suffer from the missed business opportunities and/or internal chaos. The staff who will help implement the project are also major stakeholders, as the successful implementation of effective cybersecurity controls reflects their skills and competence. The specific individuals who will implement the project may be internal employees or contractors. Many parts of your cybersecurity program may require a combination of internal and external work. For example, a new network switch and desktop computers might be installed by your internal staff, but you may need to hire an electrician to come in and install the cables. It is critical that you document all third parties that will be involved, as miscommunication with third parties can easily derail a project. Those employees and customers who will actually benefit from the cybersecurity controls are probably the most important stakeholders. The security program is designed to protect them and their data from unauthorized access. If the cybersecurity program fails, customers and employees may see their private data compromised, leading to all kinds of potential hardships.
Current State vs Future State: a great way to narrow down requirements for implementing a cybersecurity program is clearly observing and documenting the current state of your organization’s cybersecurity posture and then documenting what the desired posture should look like. In Stage 1 of this framework, you already identified much of the current state of your cybersecurity posture, so it should be rather simple for you to understand the current state. For the future state, you will need to identify the controls in this framework that you wish to implement and explain in detail what they will need to do, where they will need to go, and how they will be different than your current cybersecurity program. To identify specific requirements, all you need to do is find the differences between the future state and current state and list out the specific changes that need to be made to go from current to future.
Functional Requirements: The functional requirements explain what the specific controls do in your work environment. You will want to list each control in the program that you plan to implement, and then break each control down into specific operations, workflows, tasks, and features that will be required for success of the controls.
Non-Functional Requirements: These requirements are the specifics of how the individual pieces of the program will behave. For example, an MFA system needs to either deny or allow access to a user, provide 24/7 uptime, and be easily configured by an admin. In terms of this framework, non-functional requirements are all the different pieces that will be necessary to make controls behave the way they should.
Technical Requirements: These requirements are generally the easiest to define and you likely already have an idea of what they are. They include devices, specific pieces of hardware, software programs, licenses, and connections. To clearly identify the technical requirements, it is best to map out how each individual piece of technology will work together to allow a specific control, device, or precaution to function correctly.
In essence, Requirements Gathering is just designing a system with each type of requirement representing a different level. The technical requirements need to come together and function correctly to allow the program to perform as expected, resulting in specific tasks being completed in compliance with the greater cybersecurity program.
Or if you want a real-world example:
The new computers need to have Windows 11 Pro, a TPM, UEFI Secure Boot, and 8GB of RAM in order for BitLocker to be enabled, which will allow encryption of employee workstations in order to provide protection of Personally Identifiable Information as required by the framework.
If you list out each control like this, the requirements will become evident. Hopefully this helps you understand the process a bit more. I know project management can be difficult to explain and pretty dry to try and study.
Interview Stakeholders: You need to grasp the needs of employees and customers to understand any additional requirements that may need to be included. For example, you may be planning to require biometric face scans for passwordless authentication on all your company devices. However, you have a lot of remote workers that connect with their home devices. You ask them about the new control, and they tell you that they do not have cameras on their home computers. Now you know that you will need to purchase and provide external webcams for the employees to be authenticated. You may have completely missed this requirement if you decided to just implement the passwordless authentication at face value.
List out the Final Requirements: Your final list of requirements will be used to purchase items, follow up with third parties, and plan specific placements and designs of systems. The final list should be organized following the structure provided earlier. Start with the highest level (functional) requirements, which in turn will rely on non-functional requirements to deliver their end goal, which in turn rely on specific technical requirements to perform properly.