At this point, you should have a solid structure in place for implementing your cybersecurity program. You have completed pre-requisite documentation and arranged a team for oversight of the program. You have also started doing some project management tasks to plan out the necessary resources for smooth implementation. However, one question needs to be answered: when exactly should the controls and technologies be installed?
Networks are extremely sensitive, so it is extremely risky to try and make changes to network infrastructure in the middle of the day when employees are performing their workflows. Even if you follow installation guidelines step by step, there is bound to be some trial and error. Connectivity interruptions are almost guaranteed when making major changes to networks and systems. If your employees are in the middle of workflows when you make changes, you risk corrupting data and even destroying progress.
This is why it is key to plan maintenance windows and blackout periods. A maintenance window is a pre-scheduled time period where technology changes, updates, and tests are prioritized. This could be anything from upgrading computers to Windows 11, to installing new firewalls and wireless access points. Because maintenance windows are pre-approved, management has plenty of time to inform all employees of the window. Since network stability is not guaranteed during this time, management should recommend that employees complete all workflows before the window or simply wait until the window closes.
To plan for maintenance windows, it is crucial to gather your cybersecurity team, managers, and any third-party contractors like MSSPs or electricians. This way, all perspectives can be heard, and the maintenance windows can be scheduled for a time that clearly works for everybody. It is a terrible practice to simply throw out random times for technology maintenance and just assume that everything will come together. Maintenance windows should be planned at least a few weeks ahead of time and should be repeatable. Some business owners may decide to work on their cybersecurity program after hours, while others may prefer to do the work on weekends. Some may decide to cease normal operations for a week or so and implement the program all in one go. The time periods defined for maintenance windows are up to you and the necessary parties.
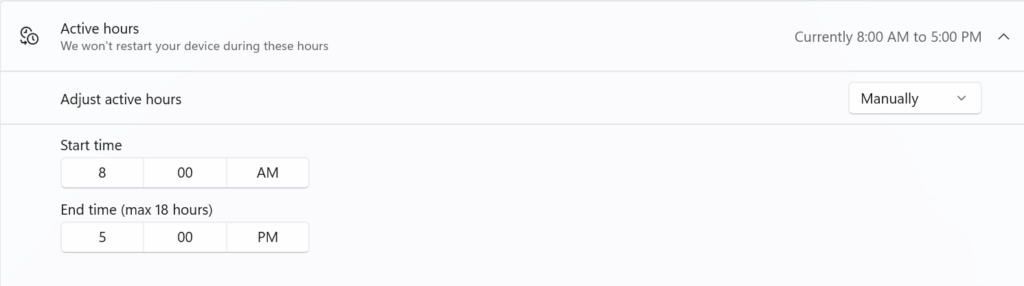
Some software applications and systems allow administrators to define maintenance windows for the software to strictly adhere to. This is especially useful for software that is configured to update automatically. For example, Windows Update allows administrators to configure “Active Hours”, the span of time during which Windows systems are being used heavily and should not be interrupted. If your employees work 9 to 5, you could specify that window of time as the Active Hours, and Windows will wait until after 5 to perform any updates.
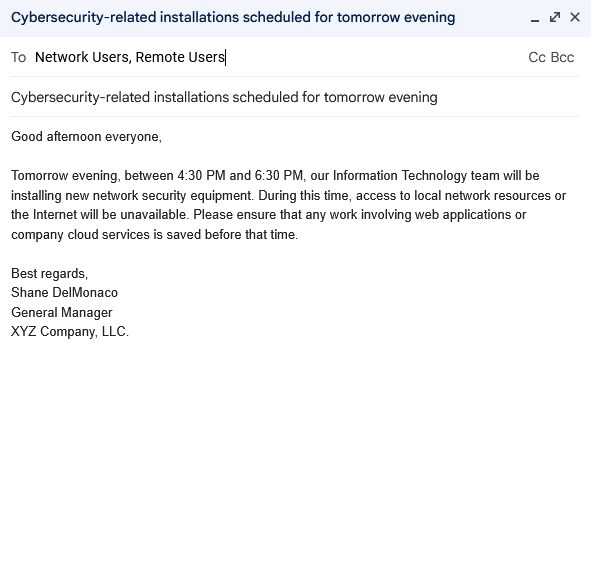
Once maintenance windows are agreed on, you need to clearly communicate them to all employees and involved parties. In earlier documentation, you identified the key communication channels to be used for relaying information related to your cybersecurity program. Probably the most common channel to communicate maintenance windows is email. Most businesses have email groups containing all employee addresses. A few days before the next maintenance window, you should send a formal email to the group reminding them of the window’s time and encouraging them to finish or cease all workflows for that time. If your maintenance windows occur regularly at the same time, you could automate the emails to be sent automatically.
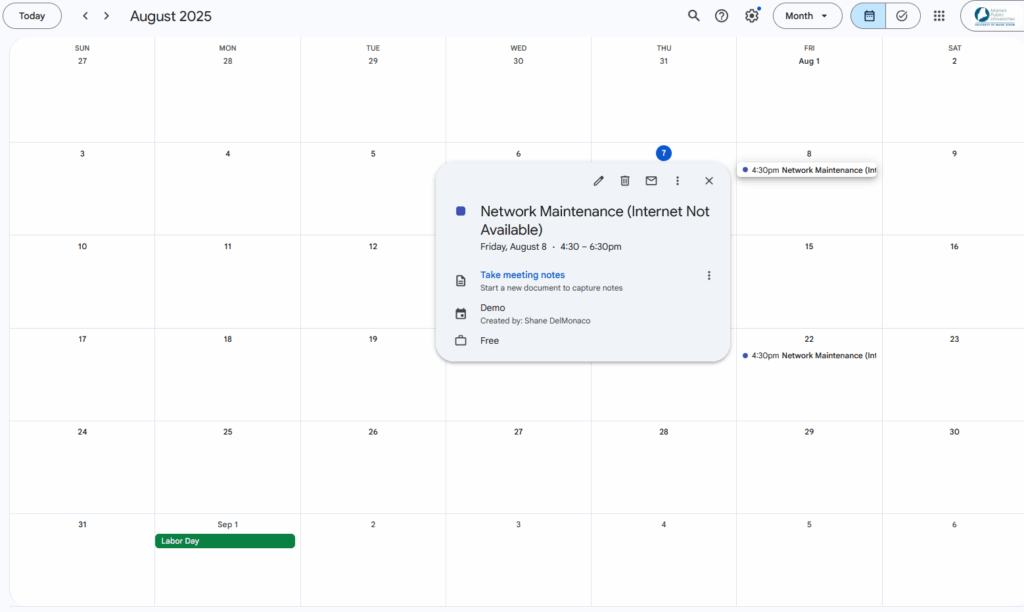
Another good communication channel is digital calendaring. Lots of businesses use platforms like Google Calendar to schedule and share events and tasks throughout the organization. If you utilize a platform like this, it’s a good idea to schedule maintenance windows on the calendars so that employees can take note of them.
A blackout period is the opposite of a maintenance window. It is a period of time where stability and availability are crucial and should not be interrupted under any circumstances. This is usually an extended period of time where business operations are at their peak, and all or nearly all systems are required to be fully functional. Because of this, technology maintenance tasks like updates, upgrades, or device configurations are strictly prohibited.
Let’s say that you run a bakery and can always expect a high degree of traffic during the weeks of Thanksgiving and Christmas. A large share of your yearly profit comes from these two weeks, and you need all Point-of-Sale systems, network connections, cloud services, and IoT devices to operate 100%. An infrastructure change that derails network connectivity for even a few hours could equate to a significant loss of productivity and profit.
Blackout periods are a bit trickier to define and schedule than maintenance windows. To many business owners, every day is a blackout period. However, in terms of implementing a cybersecurity program, a blackout period should refer to a specific period where high traffic is expected, or the volume of internal workflows is expected to increase. If you don’t have any specific time blackout periods defined off the top of your head, you might benefit from using data analysis tools or Enterprise Resource Planning (ERP) systems to gather insights.
Communicating blackout periods usually involves the same tools as communicating maintenance windows, but with a more specific audience. Most of your internal employees know of these busy periods already or are indifferent since they are not required to shift any time to accommodate them. Blackout periods should instead be clearly communicated to IT and maintenance staff. The week before Christmas, you could send out a more personalized email to your IT department, reminding them that the business is expected to be busy next week, and no major changes should be implemented. This is especially important if you use third-party IT consultants or MSSPs who may not be knowledgeable of your exact business trends.
