The CyberLadder Framework is a basic cybersecurity framework that provides small business owners with a thorough guide on hardening their cybersecurity posture. The framework seeks to take the best practices outlined in professional cybersecurity frameworks and simplify them so they address the nuances of small business environments. The CyberLadder Framework is not meant to be a replacement for professional-grade frameworks and regulations. However, it can be used in combination with many. If your organization is required to comply with standards and regulations such as HIPAA, ISO 27001, PCI-DSS, GDPR, etc, make sure you do your due diligence to comply with those frameworks first and foremost.
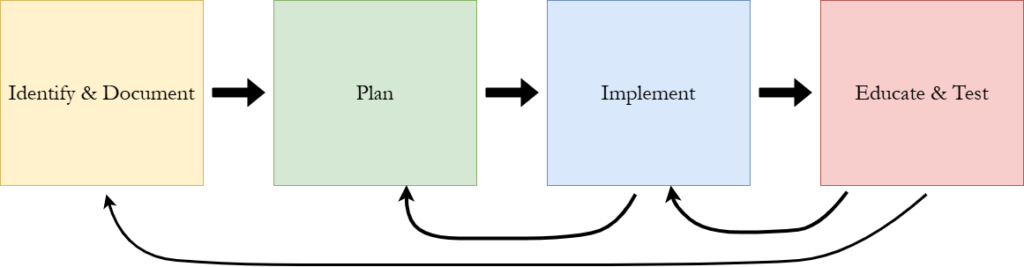
The framework consists of four stages. The four stages take you through the full process of constructing an industry-standard cybersecurity program to protect your customers, your employees, your assets, and your bottom line. An important thing to understand is that building a cybersecurity program is an ongoing, iterative process that requires continuous improvement to stay up to date with the latest threats. The CyberLadder Framework is meant to be repeated yearly, with a yearly Audit outlined in Stage 4, initiating a Stage 1 Gap Analysis, hence creating a yearly loop where the cybersecurity program is re-calibrated and improved.
A single iteration of the framework may also require going back and forth between different stages. The ultimate goal is to have a complete cybersecurity program, not a quick one. Therefore, you may find that some controls integrated in Stage 3: Implement require you to return to Stage 2: Plan to make adjustments to your initial program plan. While performing tasks in Stage 4: Educate & Test, you may also find that some controls need to be fine-tuned, hence requiring you to return to Stage 3: Implement. I have injected several project management standards into the planning stage of the framework to try and minimize scope creep and make the framework as smooth flowing as possible.
Stage 1: Identify & Document initiates the creation of the cybersecurity program by reviewing the current state of cybersecurity measures in the business environment. Inventories are made of all digital resources, including hardware, software, identities, privileges and access controls, and network infrastructure. Documentation is also made of all third-party entities involved with the environment, as well as the key stakeholders in the success of the organization's cybersecurity. This stage then requires the identification of the larger systems and data flows that make up the key day-to-day workflows that allow the organization to be successful. After a full inventory of all digital components is made, a gap analysis, business continuity plan, and risk assessment is made to identify where security is most critical and where it is most lacking. This process is supplemented with reconnaissance and security scans to identify immediate vulnerabilities. The analysis done at the closing of Stage 1 sets the groundwork planning the implementation of security controls, which will be done in the next stage.

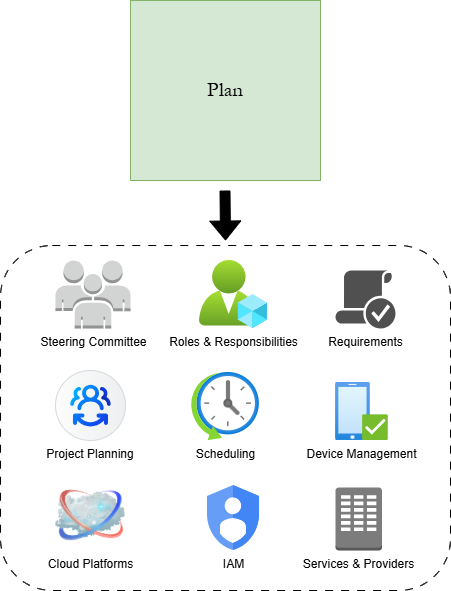
Stage 2: Plan oversees the preparation for implementing security controls to address the gaps identified in the previous stage. Planning starts by establishing a Steering Committee to ensure diverse input from all areas of the organization throughout the process of building the cybersecurity program. Roles and Responsibilities relating to cybersecurity also need to be identified to ensure stable structure in the organization. Afterwards, Stage 2 guides the organization to identify appropriate project management techniques and prepare the environment for the changes made in Stage 3. This involves comprehensive requirements gathering, scheduling of maintenance windows and blackout periods, and the creation of a staging environment to test security technologies before full implementation. After preparing the organization structure for the cybersecurity program, Stage 2 ends by presenting a variety of high-level solutions that should be considered to improve and modernize the organization's cybersecurity posture. These include embracing centralized Identity & Access Management, Identity Federation & Single Sign On across products, moving on-premises services to cloud platforms, and choosing between Workgroups, on-premises AD domains, and Mobile Device Management (MDM) for endpoint management. None of the technologies discussed in Stage 2 are required, but they are highly recommended to simplify digital resource management and make future improvements easier.
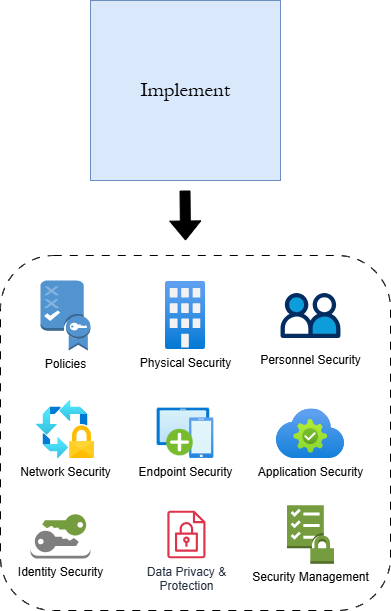
Stage 3: Implement is where cybersecurity controls are implemented into the organization. The stage begins by mandating the creation of cybersecurity policies to provide security governance at all levels. Policies govern things like acceptable use of network resources, password creation, business continuity and disaster recovery, and remote working/BYOD standards. Policies are then followed by the implementation of standards for securing the organization's premises and Human Resources practices. These controls are followed by direct technical controls for securing all areas of digital infrastructure: network hardware, systems/devices, applications, digital identities, and data. Stage 3 closes by introducing administrative practices and recommendations to assist with keeping a firm grip on the operation of new controls.
Stage 4: Educate & Test ends the process by helping administration ensure smooth implementation and use of the cybersecurity program and its associated controls. The framework understands that humans are the weakest and most vulnerable component in any security program. Thus, constant education and training need to be implemented to keep the organization secure. Employee Security Awareness Training is emphasized as a non-negotiable part of the program, with ideas for simulations and tabletop exercises provided to make education training interactive and collaborative. Changes to business culture regarding cybersecurity are also recommended, with the ultimate goal of establishing a comfortable "Culture of Security" where all employees feel comfortable voicing their opinions, concerns, and experiences. Stage 4 then shifts to the training portion. Strategies are provided for regularly testing the effectiveness of the security program and searching for emerging threats and vulnerabilities. These strategies include penetration testing, vulnerability scanning, and integration of threat intelligence sources into the workplace. Stage 4 concludes by setting a requirement for regular audits of the cybersecurity program. These Audits are essentially carbon copies of the Gap Analyses performed in Stage 1, therefore initiating another iteration of the framework when necessary.

