Microsoft Windows unanimously remains the most widely used desktop operating system in the world. Governments, private businesses, families, and individual citizens continue to trust Microsoft for their digital experiences. Being the most popular comes with downsides, and the most evident one for Microsoft is the numerous exploits that exist for its Windows operating systems.
Threat actors will usually assume that their targets are using Windows systems in their environments. While macOS holds a decent chunk of market share, and Linux is increasing its share, Windows is still the prime target for hackers.
Because of the dangers associated with the operating system, special precautions should be taken to harden Windows systems in your organization.
Choose the Professional or Enterprise Version of Windows
If you run to your local Walmart to pick up a basic PC to use for your business, it's likely to be running Windows 11 Home. Try to avoid this. For business environments, Windows 11 Pro or Enterprise should be used. The Home version lacks a wealth of features that enable extra security and configuration controls. Most consumer electronics vendors provide an option to choose between the Home and Pro versions of Windows. If you are looking to install a copy of Windows on an existing machine, you can purchase a copy of Windows 11 Pro directly from Microsoft.
Enforce Use of Standard User Accounts for Day to Day Workflows
Organizations on the medium to large side of the economy typically use Microsoft’s directory service, known as Active Directory. This service allows IT admins to centralize Windows systems and configure granular permissions, settings, and access controls.
A small business is likely to have only a handful of Windows machines. The price of Windows Server and Active Directory is tough to justify in this case.
What is likely to happen is that you or another administrator of your business will configure a Windows system with one or more user accounts. A critical security vulnerability is enabled right off the bat in Windows setup. The Windows setup, called the Out of Box Experience, directs you to create an Administrator-level account. This often results in the employees receiving the machines being given admin privileges. Nobody in any organization should be using administrator privileges for regular computer usage. The admin permissions mean that the user, or an attacker who breaches the system, can install software, damage critical system components, and much more.
Every employee, even management and owners, should do their daily tasks with a Standard account. An Administrator account should be created at setup for each computer and left unused except for necessary configuration and maintenance tasks. This security procedure is known as Least User Access (LUA).
To create Standard user accounts from the initial Windows desktop after setup, do the following:
- Open the Computer Management program.
- On the left pane, navigate to System Tools, then Local Users and Groups.
- Select the Users folder.
- Here you will see all current users. There are already some present for system-level tasks.
- To create a new user, right-click and select New User …
- Provide a username and full name for your employee following a standard convention such as first.last or first_last.
- Enter a generic password like password12345, then ensure the box is checked to “Force user to change password at next logon”.
- Click Create.
You now know how to create standard user accounts for all employees (including yourself).
Encrypt Data at Rest With BitLocker
The protection of data at rest on business systems is critical for ensuring confidentiality. BitLocker is an encryption service that allows users to encrypt the data on their hard drives. If the system happens to be physically stolen, threat actors will not be able to view the contents on the hard drive since it is encrypted. To access the drive, a user must provide a recovery key that only the proper user has access to. BitLocker can encrypt the entire drive at once or encrypt only the currently used space. It is important to note that BitLocker is only available on the Pro, Enterprise, and Education versions of Windows. Your system must also have a Trusted Platform Module and a minimum of two disk partitions.

Ensure that Windows Defender & Windows Firewall are Enabled
Windows has two built-in security services that act as defense for the system. Windows Defender (Windows Security) is the Windows built in malware scanner. Windows Defender can protect your systems against a variety of cyber threats. Defender should always be turned on unless you have implemented a separate third-party anti-malware solution. Windows Firewall is a host-based firewall appliance that allows and blocks connections to systems. While a network firewall is usually relied upon to block malicious external connections, host-based firewalls are necessary to further harden endpoints. Under no pretexts should Windows Firewall be disabled. There are three firewall states for the application: Public, Private, and Domain. All three should remain enabled to protect systems on different network security deployments.
Ensure Windows Updates are Regularly Applied
Microsoft regularly releases patches and system updates to ensure continuing functionality and security of Windows endpoints. These updates are critical for every business network. Most Windows users leave Windows Update settings at their defaults, meaning that updates are downloaded and installed according to Microsoft’s schedule. Users are usually given control over when their system should be restarted to install updates. In a larger Windows network, endpoints will usually be managed, either through Active Directory or an MDM platform like Microsoft Intune/ These deployments offer more administrative control over update deployments. If your organization utilizes one of these platforms, make sure that Windows Update management is configured in a way that suits your organization. If you are not using any centralized management solution, ensure that Windows Updates remain enabled and automatically installed.
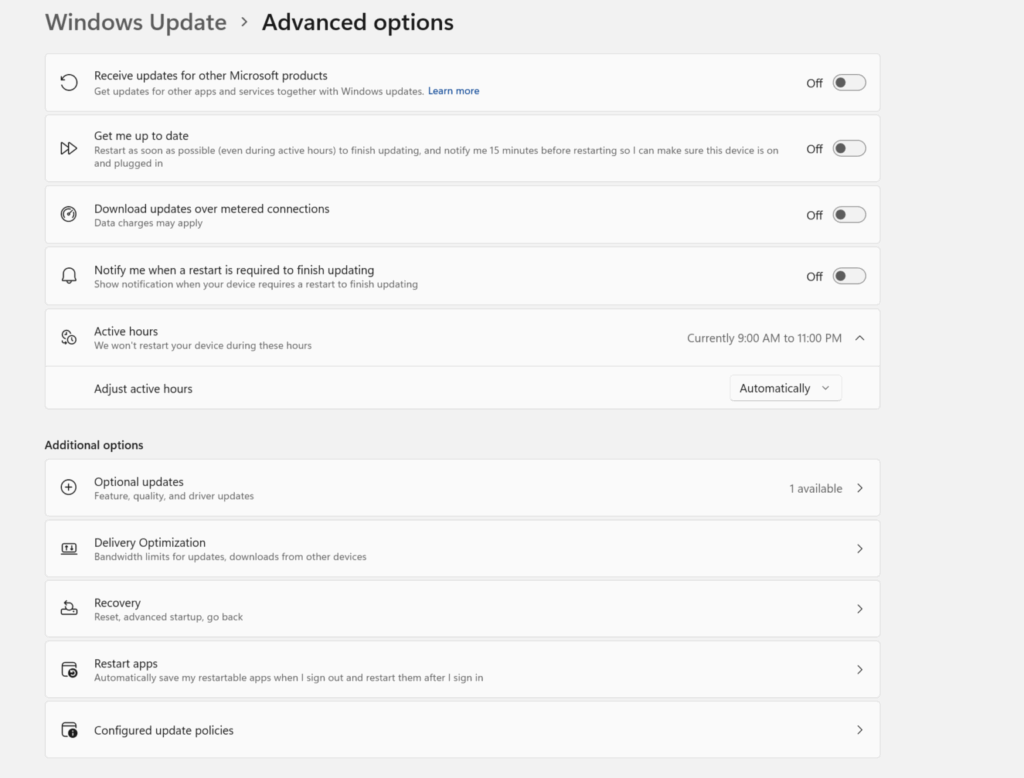
Even with local installation of Windows Updates installed, there are several settings that can be configured to improve user experience
Pause Updates: Installation of Windows Updates can be postponed for a set period, usually a few weeks.

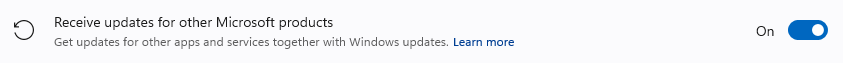
Receive updates for other Microsoft products: allow Microsoft to install updates for other Windows apps and services alongside the main updates.
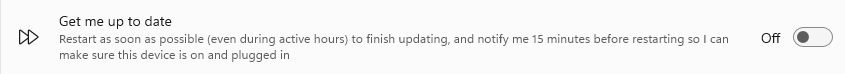
Get me up to date: allows Windows to restart as soon as possible to finish update installation; includes a 15-minute reminder.
Download over metered connections: large files like Windows updates can hog data if downloaded over a mobile network. Usually they should be turned off, but you can allow downloads over these networks if you choose.

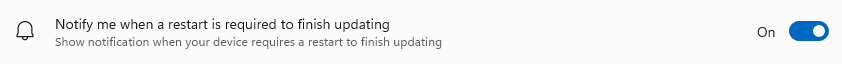
Notify me when a restart is required to finish updating: this reminds users when Windows Updates have not been completed yet and require a restart to do so.
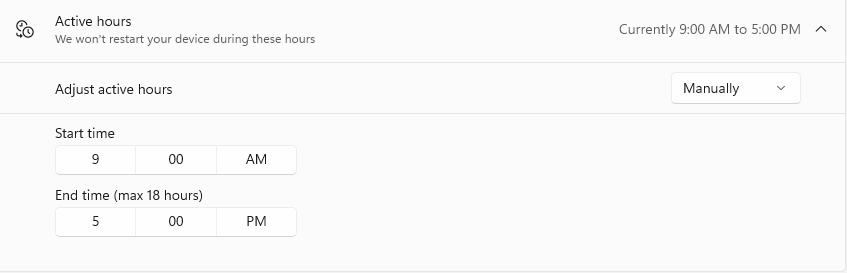
Active Hours: by setting the regular working hours of your organization, you can prevent any restarts from being applied during this time frame.
GPOs & Benchmarks
Organizations that run an Active Directory domain usually enforce a range of security settings through the use of Group Policies. You should already be familiar with the basics of Group Policy from earlier documentation. However, even devices arranged in a Workgroup without a centralized domain structure have Group Policy capability. Standalone Windows Pro, Enterprise, and Education systems have a Local Group Policy editor that can be used to assign security settings to the local computer. In addition the Windows system policies, GPOs can be used to set security settings for several applications. This is done by downloading the official ADMX/ADML templates for the applications and importing them into the Policy Definitions folder on the Windows device. Chrome, Firefox, Zoom, and Office 365 are examples of software applications that have publicly available templates for GPOs.
Many organizations, both public and private, follow Security Benchmarks when assigning Group Policies. A benchmark is a collection of best practice settings for a specific product that can be assigned at a high level to uphold security for that product throughout the organization. The Center for Internet Security is known for its collection of thorough benchmarks for securing a variety of systems and applications. By registering with CIS, you can obtain access to the benchmarks and have a direct roadmap for implementing them in your environment. Another well-known producer of benchmarks is the US Department of Defense (DoD), which uses the STIG format to share its baselines.
As a small business owner, you likely do not want to spend time going through and configuring benchmark settings on a handful of devices within your organization. This is understandable, as many benchmarks can be very long and thourough. As part of this framework, I have produced a Local Group Policy containing a mix of best practice security settings from both CIS and DoD benchmarks. This LGPO has been provided below for download free of charge. With this, you can simply go to each Windows system in your organization and import the LGPO, provisioning your devices in just a matter of minutes. A full step by step guide on how to do this is also provided. Ensure that you consult the documentation provided with the LGPO to see the exact settings that have been configured.
